
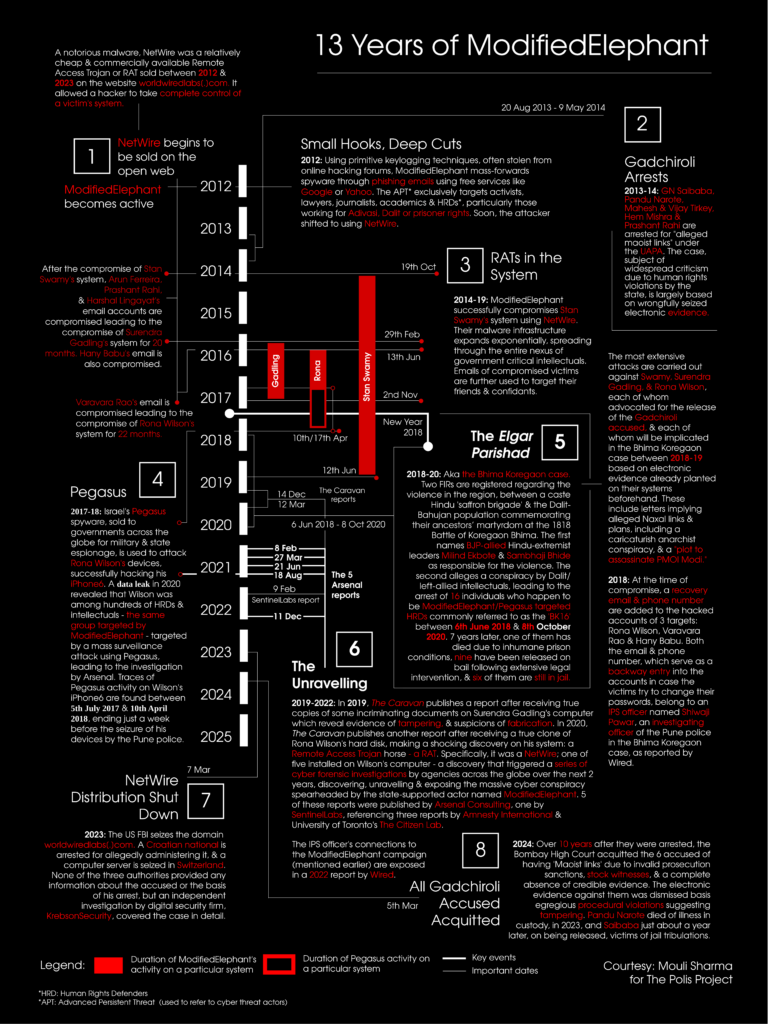
A complete chronology of the seven-year-long cyberattack (and it’s slow, horrific unravelling) carried out by the same threat actor against 16 human rights activists, who were resultantly incarcerated without trial under the UAPA for the alleged orchestration of the Bhima Koregaon violence at the start of 2018 and a made up plot to assassinate the prime minister of India. Christened by security firm Sentinel in 2022 after a series of tech investigations starting in 2019 with the discovery of a Trojan horse on researcher Rona Wilson’s seized system, the notorious ModifiedElephant has been targeting activists and HRDs in India since at least 2012 using extremely rudimentary means of surveillance, remote access, and file delivery, and worked directly with the Pune police (using IPS officer Shivaji Pawar’s contact information as its backway into the hacked systems) to frame members of the BK16. Worse still, the Pune FSL also protected ModifiedElephant, omitting crucial and unmistakable evidence of what was not only an astoundingly severe hackjob, but also—importantly—an astoundingly sloppy one, from its reports of forensic analysis of the devices.
Activists who have been confirmed to have been hacked within the ModifiedElephant campaign against the BK16:
- Stanislaus Lourduswamy: 56 Months
- Varavara Rao: Unknown Duration
- Arun Ferreira: Unknown Duration
- Harshal Lingayat: Unknown Duration
- Prashant Rahi: Unknown Duration
- Rona Wilson: 22 Months
- Surendra Gadling: 20 Months
Basic timeline of ModifiedElephant’s operation:
- 2012: The beginnings of ModifiedElephant, NetWire: Using primitive keylogging techniques, often stolen from online hacking forums, ModifiedElephant mass-forwards spyware through phishing emails using free services like Google or Yahoo. An APT (Advanced Persistent Threat), ModifiedElephant exclusively targets activists, lawyers, journalists, academics and HRDs, particularly those working for Adivasi, Dalit or prisoner rights. The same year, a notorious malware, NetWire was a commercially available Remote Access Trojan or RAT sold between 2012 and 2023. It allows a hacker to take complete control of the victim’s system.
- 2013-14: Gadchiroli arrests take place: Lt. Prof. GN Saibaba, Lt. Pandu Narote, Hem Mishra, Mahesh Tirki, and Prashant Rahi are arrested for “alleged Maoist links” under the UAPA. The case, subject of widespread criticism due to human rights violations by the state, is largely based on illegally seized electronic evidence.
- 2014-19: Wide-scale use of NetWire RAT begins against Indian HRD nexus: ModifiedElephant successfully compromises Stan Swamy’s system using NetWire. Their malware infrastructure expands exponentially, spreading through the entire nexus of government critical intellectuals. Emails of compromised victims are further used to target their friends and confidants.
After the compromise of Stan Swamy’s system, Arun Ferreira, Prashant Rahi, and Harshal Lingayat’s email accounts are compromised leading to the compromise of Surendra Gadling’s system for 20 months. Additionally, Hany Babu’s email is also compromised. Varavara Rao’s email is compromised leading to the compromise of Rona Wilson’s system for 22 months.
The most extensive attacks are carried out against Swamy, Surendra Gadling, and Rona Wilson, each of whom advocated for the release of the Gadchiroli accused, and each of whom will be implicated in the Bhima Koregaon case between 2018-19 based on electronic evidence already planted on their systems beforehand. These include letters discussing alleged Naxal links and a “plot to assassinate Narendra Modi.” At the time of compromise, a recovery email and phone number are added to the hacked accounts of 3 targets: Wilson, Rao and Babu. Both the email and phone number, which served as a backway entry into the accounts in case the victims tried to change their passwords, belonged to an IPS officer named Shivaji Pawar, who would eventually be an investigating officer of the Pune police in the Bhima Koregaon case.
- 2017-18: Pegasus: Israel’s Pegasus spyware, sold to governments across the globe for military and state espionage, is used to attack Rona Wilson’s devices, successfully hacking his iPhone6. A data leak in 2020 revealed that Wilson was among hundreds of HRDs and intellectuals – the same group targeted by ModifiedElephant – targeted by a mass surveillance attack using Pegasus, leading to the investigation by Arsenal. Traces of Pegasus activity on Wilson’s iPhone6 are found between 5th July 2017 and 10th April 2018, ending just a week before the seizure of his devices by the Pune police.
- 2018-20: Elgar Parishad: Also known as the Bhima Koregaon case. Two FIRs are registered regarding the violence in the region, between a caste Hindu ‘saffron brigade’ and the Dalit-Bahujan population commemorating their ancestors’ martyrdom at the 1818 Battle of Koregaon Bhima. The first names BJP-allied Hindu-extremist leaders Milind Ekbote and Sambhaji Bhide as responsible for the violence. The second alleges a conspiracy by Dalit/left-allied intellectuals, leading to the arrest of 16 individuals who happen to be ModifiedElephant/Pegasus targeted HRDs commonly referred to as the ‘BK16’ between 6th June 2018 and 8th October 2020. 7 years later, one of them has died due to inhumane prison conditions, nine have been released on bail following extensive legal intervention, and six of them are still in jail.
- 2019-22: Discovery and Unravelling of ModifiedElephant Malware Infrastructure: In 2019, The Caravan publishes a report after receiving true copies of some incriminating documents on Surendra Gadling’s computer which reveal evidence of tampering, and suspicions of fabrication. In 2020, The Caravan publishes another report after receiving a true clone of Rona Wilson’s hard disk, making a shocking discovery on his system: a Remote Access Trojan horse – a RAT. Specifically, it was a NetWire; one of five installed on Wilson’s computer – a discovery that triggered a series of cyber forensic investigations by agencies across the globe over the next 2 years, discovering, unravelling and exposing the massive cyber conspiracy spearheaded by the state-supported actor named ModifiedElephant. 5 of these reports were published by Arsenal Consulting, one by SentinelLabs, referencing three reports by Amnesty International and University of Toronto’s The Citizen Lab.
The IPS officer’s connections to the ModifiedElephant campaign (mentioned earlier) are exposed in a 2022 report by Wired.
- 2023: NetWire Distribution Website Seized: The US FBI seizes the domain worldwiredlabs[.]com. A Croatian national is arrested for allegedly administering it, and a computer server is seized in Switzerland. None of the three authorities provided any information about the accused or the basis of his arrest, but an independent investigation by digital security firm, KrebsonSecurity, covered the case in detail.
- 2024: Acquittal of Gadchiroli Accused: Over 10 years after they were arrested, the Bombay High Court acquitted the 6 accused of having ‘Maoist links’ due to invalid prosecution sanctions, stock witnesses, and a complete absence of credible evidence. The electronic evidence and other documentary evidence against them was squarely dismissed on account of egregious procedural violations suggesting mala fide tampering and the planting of incriminating documents. Pandu Narote died of illness in custody, in 2023, and Saibaba just about a year later, on being released, both victims of jail tribulations.
Comparative analysis of the attacks against Stan Swamy, Surendra Gadling and Rona Wilson (herein termed ‘Arsenal Reviewed Attacks’)
| Criteria/Victim | Stan Swamy | Surendra Gadling | Rona Wilson |
| Start of Compromise | 19th October 2014 | 29th February 2016 | 13th June 2016 |
| End of Compromise | 12th June 2019 | 2nd November 2017 | 17th April 2018 |
| Duration (in months) | 55 months, 24 days | 20 months, 4 days | 22 months, 4 days |
| Date of Seizure | 12th June 2019 | 17th April 2018 | 17th April 2018 |
| Date of Seizure same as End of Compromise? | Yes | No | Yes |
| Number of NetWire RATs | 12 | 10 | 5 |
| Nature of Attack | Long-term Surveillance and Incriminating Document Delivery | Long-term Surveillance and Incriminating Document Delivery | Long-term Surveillance and Incriminating Document Delivery |
| Surveilled Data | Browsed websites, submitted passwords, composed emails, and edited documents. | Browsed websites, submitted passwords, composed emails, and edited documents. | Browsed websites, submitted passwords, composed emails, and edited documents. |
| Location of Document Delivery | Hidden folder named ‘mydata’ | Hidden folder named ‘Material’ | Hidden folder named ‘Rbackup’ |
| Location of stolen files | Synchronised C2 server | Synchronised C2 server | Synchronised C2 server |
1. Caravan Report I – Police Tampering Raises Suspicions
14 December 2019: Caravan published a report analysing documents of police procedure and metadata of incriminating files on Surendra Gadling’s computer, provided to him by the prosecution through the relevant court, showing evidence of tampering and suspicious activity: the alignment of the text of an incriminating document was changed while the computer was under police custody, and all incriminating files were cut and pasted from various locations into a single folder on the desktop—where the police claim to have discovered them—within a span of 1 minute and 48 seconds on 7 December 2017. It also highlighted the selective violation of cyber evidence procedure[1], specifically the failure to record hash values corresponding to devices at time of seizure, with reference to the only devices on which ‘incriminating files’ were later found. Another noted inconsistency is that the incriminating files have been intercepted in the form of saved documents instead of emails where there could have been third-party verifiability regarding and complete track of the authors and receivers of the files. This is especially relevant in view of the fact that the majority of files found on Gadling as well as two of his co-defendant’s devices—Rona Wilson and Stan Swamy—on the basis of which they are accused, as noted in the first, third and fifth Arsenal reports, are correspondence documents.
2. Caravan Report II – Discovery of a Trojan
12 March 2020: After receiving a copy of Wilson’s hard disk, which had been presented in court by the Pune Police and supplied to all the accused, Caravan published another report by editor Martand Kaushik and software engineer Anjaneya Sivan based on their forensic investigation of the drive. The investigation revealed the presence of a malware on Wilson’s system, Win32:Trojan-Gen, capable of gathering protected information such as usernames and passwords, general surveillance, and remote access. The lattermost qualifies it as a Remote Access Trojan, or RAT, later identified as the infamous NetWire[2] by Arsenal Consulting.
The examination also revealed evidence of a clean-up of metadata, such as software logs, Windows explorer history, as well as document access history, all of which could have been used to track the use of the incriminating files and in turn, exonerate the accused. Another important discrepancy was the version of MS Word on Wilson’s computer, Word 2007, while the incriminating PDF documents found on his computer, which he was also accused of having authored, were created in either Word 2010 or 2013. The report highlighted that these findings had been notably omitted from the reports of the Regional Forensic Science Laboratory (RFSL), Pune.
Based on these findings, The Caravan made several speculations which were conclusively confirmed by a US based forensic firm called Arsenal Consulting in a series of five reports beginning in early 2021:
- That the discovery of a RAT on Wilson’s disk indicated the possibility of the devices of his co-accused being compromised as well, including those of Surendra Gadling, and emphasised the prosecution’s unwillingness to provide a copy of the disk as an obstacle to confirming the same. This was confirmed in the third Arsenal report, revealing that Gadling’s computer had been compromised for just over 20 months by the same attacker using the same RAT as in the case of Rona Wilson.
- That the malware may have been delivered to Wilson’s computer through malicious email or messaging links, and since it launched itself automatically on every start up, had been active on the device since long before it was seized. This was confirmed in the first Arsenal report, and the date of first compromise was found to be 13 June 2016.
- That the 10 incriminating documents on Wilson’s computer, including the sensational letter discussing an alleged plot to assassinate the prime minister and an uncanny purchase of sophisticated arms and ammunition for the CPI (Maoist), may have been planted using the aforementioned malware. This was confirmed in the first Arsenal report[3].
- That the deletion of metadata may be indicative of an intentional clean-up of evidence of ‘mischief by an investigative agency’ and of external implantation of evidence, which would enable the exoneration of the accused if it could be proven that the files were never in fact used, opened, or modified by him. This was confirmed in the first Arsenal report via an analysis of Object Identifiers, which demonstrated that the incriminating files had indeed never been ‘interacted with in a legitimate way’[4].
- That any version of MS Word more recent than the 2007 version had never been installed on Wilson’s computer, the only one in his possession, suggesting that he could not have authored the files[5]. This was confirmed in the first Arsenal report through an ‘aggressive search’ of Windows Registry information from Volume Shadow Copies, unallocated space, and elsewhere.
3. Arsenal Consulting Report I – Rona Wilson: An Unbelievable Malware Infrastructure
8 February 2021: Arsenal Consulting was retained by Wilson’s defence team to further analyse the seized electronic evidence, including his computer hard disk and a removable Cruzer blade. The executive summary of the report by Mark Spencer stated the following:
Rona Wilson’s computer was compromised for just over 22 months. The attacker responsible for compromising Mr. Wilson’s computer had extensive resources (including time) and it is obvious that their primary goals were surveillance and incriminating document delivery. Arsenal has connected the same attacker to a significant malware infrastructure which has been deployed over the course of approximately four years[6] to not only attack and compromise Mr. Wilson’s computer for 22 months, but to attack his co-defendants in the Bhima Koregaon case and defendants in other high-profile Indian cases[7] as well. It should be noted that this is one of the most serious cases involving evidence tampering that Arsenal has ever encountered, based on various metrics which include the vast timespan between the delivery of the first and last incriminating documents.
In detail, the analysis confirmed The Caravan’s various speculations as listed above, and discovered 4 RATs on the system in addition to the one discovered by Caravan. The chain of events starting with the compromise of Wilson’s computer leading up to the delivery of the final incriminating document and seizure of devices is as follows:
- 13th June 2016: Wilson’s computer is compromised through malicious links to a C2 (‘command and control’) server sent using Varavara Rao’s compromised email[8], which leads to the installation of NetWire on his device.
- 27th April 2016 to 30th October 2016: Five NetWire samples are wrapped on Wilson’s system, two of which are obfuscated. Between the creation of the last sample and the seizure of Wilson’s devices on 17th April 2018, these samples are used to heavily monitor his device use: ranging from browser history, password entry, to even simply documents being typed. This is done by synchronising the disk and two attached devices to C2 servers, including the seized Cruzer blade, using various additional tools.
- 3rd November 2016: The folder ‘kbackup’ is remotely created, renamed to ‘Rbackup’, and set to ‘hidden’. This hidden folder is where the ‘top ten most incriminating files’ (hereafter also ‘incriminating document(s)’ or collectively the ‘top ten’) were eventually delivered via NetWire, along with various other documents from Wilson’s system which were copied into it. The latter act is described in the report as “consistent with an attacker better obscuring forged documents amongst ‘noise’.”
- 29th March 2017 to 28 January 2018: Nine of the ‘top ten’ are delivered to the hidden folder Rbackup. They are delivered in the form of .rar archives unpacked by a version of WinRAR specifically deployed for the purpose of the attack (both of which will later be deleted), different from another WinRAR present in the system, which has a history of legitimate use. Following are 9 of the ‘top ten’ documents in chronological order of delivery.
- Incriminating Document 1 – Ltr_2_RW.pdf: Created on 29 March 2017 (11:03:01 IST) via NetWire attack. Summarised by Arsenal as follows:
Alleged letter from “Prakash” to “Comrade” mentioning failure of support among the people and “Comrade H.B.” taking over present and future tasks of “RDF.” The letter ends by discussing outreach to students of DUSU/JNUSU and “… it is on the shoulders of these young revolutionaries the future People’s War will be fought.” This document is in English.
-
- Incriminating Document 2 – Ltr_1804_to_CC.pdf: Created on 20 April 2017 (00:13:41 IST) via NetWire attack. This is the most incriminating of the ‘top ten’, and contains the alleged plot to assassinate India’s Prime Minister Narendra Modi and the uncanny purchase of sophisticated arms and ammunition. Summarised by Arsenal as follows:
Alleged letter from Rona Wilson to “comrade Prakash” mentioning a meeting which resulted in a requirement for 80 million rupees (approximately 1 million US dollars) annually to obtain M4 carbines (rifles with short barrels) and 400,000 rounds of ammunition. The letter also mentions taking “… concrete steps to end Modi-raj… along the lines of another Rajiv Ghandi type incident.” This document is in English. (sic)
-
- Incriminating Document 3 – Ltr_2704.pdf: Created on 5 May 2017 (21:31:58 IST) via NetWire attack. Summarised by Arsenal as follows:
Alleged letter from Comrade Surendra to Comrade Prakash outlining Surendra’s meeting on April 22, 2017 with a respected comrade from Chhatisgarh in Delhi, and handing over funds transferred via hawala for Bastar and Maharashtra “operations.” This document is in Hindi. (sic)
-
- Incriminating Document 4 – Ltr_2_P-51117.pdf: Created on 25 December 2017 (22:30:39 IST) via NetWire attack. Summarised by Arsenal as follows:
Alleged letter from Comrade Surendra to Comrade Prakash outlining contact with a Comrade Hemu for some “A.P.T materials.” Also mentions Comrades JRC and Pervaiz, and establishing an “IAPL” organization in Kerala. This document is in Hindi.
-
- Incriminating Document 5 – Ltr_2312_to_CC.pdf: Created on 25 December 2017 (22:31:01 IST) via NetWire attack. Summarised by Arsenal as follows:
Alleged letter from Rona Wilson to “comrade Prakash” explaining a focus on efforts to better understand “fake encounters” from Gadchiroli and raising awareness of political murders of journalists. The letter also mentions efforts to address schools and colleges with information concerning mob lynching and political murders. This document is in English.
-
- Incriminating Document 6 – Ltr_2612_to_CC.pdf: Created on 27 December 2017 (21:30:37 IST) via NetWire attack. Summarised by Arsenal as follows:
Alleged letter from Rona Wilson to “comrade Prakash” mentioning a supplier in Nepal and getting the “… equipment ready on the ground.” This letter also mentions a pressing need to “inflict heavy damage on the enemy forces” and transporting the “equipment” disassembled and concealed amongst “heavy electronics appliances.” This document is in English.
-
- Incriminating Document 7 – Ltr_from_Com.M_022018.pdf: Created on 06 January 2018 (02:05:39 IST) via NetWire attack. Summarised by Arsenal as follows:
Alleged letter from “Com. M” to “Comrade Rona” mentioning “PGP material”, possibly sending “CC comrades” to meet Swedish delegates in London, and “Dalit sentiments are clearly against the Brahmin-centered agenda of BJP/RSS, this should be converted into large scale mobilization and chaos.” This document is in English.
-
- Incriminating Document 8 – CC_letter – 08Jun.pdf: Created on 21 January 2018 (14:16:05 IST) via NetWire attack. Summarised by Arsenal as follows:
Alleged letter from “comrade M.” to “comrade Surendra.” The first part of this letter refers to complaints from the Delhi Women cadre and the party leadership taking gender bias, patriarchy, and authoritarian tendencies within the “MO” leadership seriously. The second part of this letter refers to setting up a day-long program on the theme of the 50th anniversary of the Naxalbari movement. This document is in English.
-
- Incriminating Document 9 – Ltr_2_SG-27.1.2018.pdf: Created on 28 January 2018 (19:14:01 IST) via NetWire attack. Summarised by Arsenal as follows:
Alleged letter from “B.A.S.” to “comrade Surendra.” This letter describes various expenses and financial arrangements. It also mentions being sent a “… new young boy (who has been living a military life for a year)” and “Once you were to sit with him for the first time, the doctor agreed to send a boy for 6 months in the jungle.” This document is in English.
- 14th March 2018: Before the delivery of the tenth document, several nesting attempts, transfers, and creation of dummy folders and files are performed from the system to the seized Cruzer blade, activities described in the report as “consistent with an attacker realizing [traceability/visibility of their activity] and/or deciding to more deeply nest the forged documents so that the victim would not stumble upon them.” The names of the dummy files match those found in the folder from which the first NetWire sample was originally launched, suggesting a continuity in carrying out the change.
- 6th April 2018: The tenth and final of the ‘top 10 incriminating’ documents is delivered, which is as follows:
- Incriminating Document 10 – Ltr_2_Anand_E.pdf: Created on 6 April 2018 (00:00:57 IST) via NetWire attack. Summarised by Arsenal as follows:
Alleged letter from “Prakash” to “Comrade Anand” mentioning the “CC” leadership being pleased with “… the progress that you have made on the Dalit Campaign.” This letter also mentions “International campaigns can give more traction to domestic chaos” and coordination with international friends. This document is in English.
- 16 April 2018: The final changes were made to the hidden ‘Rbackup’ folder, a modification to the MFT or Master File Table made at 16:50:41 IST, just one day prior to the seizure of the devices.
In addition to painstakingly reconstructing this chain of events, the report also identified several indicators of compromise that were related to the same attacker, which matched with indicators found in forensic images of devices belonging to Wilson as well as his co-defendants. These indicators included seven hostnames, 25 C2 IP addresses, all belonging to the infamous VPS HostSailor, as well as several file names with corresponding hash values. Through these indicators, alongside catching the attacker red-handed in its second and third report respectively, Arsenal discovered that the attacker is connected to an extensive malware infrastructure, and has been part of multiple campaigns using NetWire and DarkComet. In 2022, this work would form the basis for an AI based security firm called SentinelOne to further investigate this attacker and malware infrastructure, successfully connecting them to a notorious threat actor within India, who they would name ‘ModifiedElephant APT (Advanced Persistent Threat), that specifically targeted human rights activists, lawyers and defenders using commercial RATs and consistent modus operandi with the primary objective of long term surveillance culminating in the planting of fabricated incriminating evidence. The report would find that the APT had been active since at least 2012.
4. Arsenal Consulting Report II – Rona Wilson: Unfinished Incrimination and Footprints All Over
27 March 2021: Building on the investigation of the first report, the second continued its analysis of Rona Wilson’s hard disk and removable Cruzer blade, focusing on the 24 ‘additional files of interest’ – hereafter also referred to as ‘file(s) of interest’ or collectively the ‘additional 24’ – used to build the charges against him and his co-accused, in addition to the ‘top 10 most incriminating documents’ that have been established above as planted, most probably fabricated, and never interacted with. The executive summary of the second report is as follows:
Arsenal has determined that there is no evidence of legitimate interaction with the additional files of interest on Mr. Wilson’s computer, and that 22 of the 24 of the files are directly connected to the attacker identified in Report I. Arsenal has also provided a “process tree” with this report which effectively caught the attacker red-handed, by revealing both how NetWire and a temporarily deployed UnRAR[9] (from WinRAR v4.20) were used to deliver an additional file of interest to a hidden folder on Mr. Wilson’s computer, also capturing a command-line syntax mistake (and quick correction) made by the attacker. Details regarding how Mr. Wilson’s computer was initially compromised, and the attacker’s malware infrastructure, can be found in Report I.
The report concluded that the 24 additional files, just like the top ten most incriminating documents, were never interacted with in any legitimate capacity, and all but two of them were delivered into the system via NetWire and no other means, into the same hidden folder ‘Rbackup’, and by the same attacker[10]. The remaining two had suspicious sources. The deliveries were made between 25 December 2017 and 2 March 2018. 7 of the files were also discovered on the Cruzer blade, transferred on the 14th of March 2018.
Out of the 24 files, two were identified to be the same file renamed about 14 hours after its delivery, and 10 were contained within a .rar file delivered on 11 February 2018 directly through NetWire, and were never unpacked on the system. So, in total, the 24 files of interest constitute only 13 distinct deliveries: 11 through NetWire, and 2 identified as ‘suspicious’[11]. The latter two were picsdk.rar: a RAR archive which appears to contain photographs of Maoist party PLGA guerrillas, and mobile.rar: RAR archive which appears to contain a photograph of Milind Teltumbde, created on 22 January 2018 (20:09:40 IST) and 01 February 2018 (19:30:45 IST) respectively.
The 13 NetWire deliveries (described below as ‘Deliveries 1-11’) to Rbackup, including the .rar archive that was not unpacked and contained the remaining 10 files of interest, in chronological order of delivery are as follows:
- Delivery 1 – docs.rar: Created on 25 December 2017 (22:28:49 IST), a RAR archive which contained “Letter.pdf” and was deleted after unpacking was complete.
- Delivery 2 – Letter.pdf: Created on 25 December 2017 (22:29:50 IST), a minute after Delivery 1, and is the file contained within it. Arsenal’s summary of the document is as follows:
Alleged letter from “Ki” to “A” on October 17, 2017. Includes congratulations on Maoist party’s 13th anniversary and directs “A” to have a “picnic” regarding the work of Anti-Fascist Front. This document is in Hindi. (sic)
- Delivery 3 – Final_Dispatch.rar: Created on 27 December 2017 (21:23:45 IST), a RAR archive which contained “Final_Dispatch.pgp” and was deleted after unpacking was complete.
- Delivery 4 – Final_Dispatch.pgp: Created on 27 December 2017 (21:30:55 IST), seven minutes after Delivery 3, and is the PGP-encrypted file contained within it.
- Delivery 5 – mohila meeting jan.rar: Created on 11 January 2018 (11:39:40 IST), a RAR archive which contained “mohila meeting jan.pdf” and was deleted after unpacking was complete.
- Delivery 6 – mohila meeting jan.pdf: Created on 11 January 2018 (11:42:02 IST), less than three minutes after Delivery 5, and is the file contained within it. Arsenal’s summary of the document is as follows:
Alleged “mohila” (women in Hindi/Bengali) meeting minutes from January 2, 2018. Contains a list of Maoist party members, names of some Jawaharlal Nehru University ex-student leaders, and names of organizations like “JAC”, “JAGLAG”, “IAPL”, “CPDR”, and “DSU”. Mentions “Intensify tactical training for women PLGA members including booby traps/directional mines” and contains suggestions from “SG” regarding various matters. This document is in English. (sic)
- Delivery 7 – Accounts2k17.rar: Created on 1 February 2018 (22:47:19 IST), a RAR archive delivered alongside “Accounts2k17.txt” and then deleted.
- Delivery 8 – Accounts2k17.txt: Created on 1 February 2018 (22:48:48 IST), a minute and a half after Delivery 7, and is the file contained within it. Arsenal’s summary of the document is as follows:
Alleged details of funds transferred amongst Maoist party members. Contains details of transfers involving “Milind”, “Surendra”, “Shoma”, “Sudhir”, “Anand”, “Rona”, “Arun”, “VV”, and others. This text file is in English. (sic)
- Delivery 9 – IMPCorres.rar: Created on 11 February 2018 (15:41:17 IST), RAR archive containing “for your drafts.txt”, “Letter_to_GN_30July.pdf”, “ltr_CC_2_P.pdf”, “Received Naveen.doc”, “special.doc”, “JP resolution.doc”, “Letter to G.doc”, “Loans to be cleared and future programmes.xls”, “Note.doc”, and “Report on Gautam Navlakha.doc” (their contents are detailed below). This archive was never unpacked[12], and hence not deleted.
- Delivery 10 – NXPICS.rar: Created on 24 February 2018 (02:13:23 IST), a RAR archive renamed to DKComrades.rar, never unpacked, which appears to contain photographs of Maoist party PLGA guerrillas.
- Delivery 11 – ltr_from_Prakash.rar: Created on 2 March 2018 (01:31:00 IST), a RAR archive containing “Ltr_from_Prakash.pdf”, never unpacked, and summarised by Arsenal as follows:
[Ltr_from_Prakash.pdf] is an alleged letter from “Prakash” to “Rona”. Gives approval of a program on “Naveen Babu” at JNU. Refers to “Surendra”, “Sudha”, “Gadchiroli”, “Mahesh Raut”, and “Sudhir”. Mentions that the Bhima Koregaon movement is getting weaker and discusses party initiatives to strengthen it in BJP-ruled states, in order to hit the BJP in 2019 elections. Also mentions using PGP to exchange messages and destroying the letter immediately so that the enemy does not get ahold of it. This document is in Hindi. (sic)
Looking at the file names above together illustrates ModifiedElephant’s methodology of delivery. The 10 files further contained within the .rar archive created in Delivery 9 (below termed unretrieved files 1-10) in no particular order (as they were transferred collectively in the archive and have no date of creation due to never being unpacked on the system), as summarised by Arsenal, are as follows:
- Unretrieved File 1 – for your drafts.txt:
A text file that mentions “For your drafts use only” along with an email account username and password. This text file is in English. (sic)
- Unretrieved File 2 – Letter_to_GN_30July.pdf:
Alleged letter from “Sudarshan” on July 30, 2017 to “Gautam Ji”. Mentions state repression and says “The CC is well aware of the ground realities and difficulties faced by our comrades and party activists from CLC, PUDR, CDRO and other civil rights organizations while they are on FF missions in Bastar.” Also mentions contacting Comrade Surendra and defeating “fascist forces both politically and otherwise”. This document is in English. (sic)
- Unretrieved File 3 – ltr_CC_2_P.pdf:
Alleged letter from “dada” (brother in Hindi/Bengali) to “Prashant” on February 10, 2017 on Maoist party Central Committee letter head. Mentions state repression and problems in communicating. Requests that legal work be sped up for particular jailed activists. Shares concerns about “Sai” and the present situation of “CRPP” in Delhi. Also requests that “SG” call on the “safe number” on particular days and times before the “final hearing”. This document is in English. (sic)
- Unretrieved File 4 – Received Naveen.doc:
Alleged letter from “Anand” on May 7, 2015 as a reply to a letter from “Naveen”. Mentions problems coordinating with “legal mass” organizations in urban areas and updates on various military matters. Concludes with “Please destroy immediately after reading”. This document is in English. (sic)
- Unretrieved File 5 – special.doc:
Alleged letter from “Mahesh” to “Comrade General Secretary” of the Maoist party. The letter writer complains about his expulsion from the party while jailed, and mentions that while he broke under torture, he “guarded the major secrets”. This document is in English. (sic)
- Unretrieved File 6 – JP resolution.doc:
Document containing possibly obfuscated text as well as four sets of contact information. (sic)
- Unretrieved File 7 – Letter to G.doc:
Alleged letter to “Comrade” that mentions coordination of international Maoist movements. Contains details about meetings held in 2010 (Greece), 2011 (Germany) and 2012 (Greece). Includes suggestions provided at the last meeting. This document is in English. (sic)
- Unretrieved File 8 – Loans to be cleared and future programmes.xls:
Spreadsheet that lists “Programmes” (“All India Cordination against Military Deployment”, “Maoism Seminar”, etc.) and expenses, as well as loans which need to be paid back urgently. This spreadsheet is in English. (sic)
- Unretrieved File 9 – Note.doc:
Document which contains what appears to be a preliminary secret encoding of cities, date/times, individuals names (including “VV” and “Anand Teltumbde”), organization names, and passwords. This document is in English. (sic)
- Unretrieved File 10 – Report on Gautam Navlakha.doc:
Document which contains “A report on Gautam Navlakha (GN)”. This document includes a history of various interactions with “GN”. Mentions “VV” multiple times – for example: “He again walked out after his attempts to convince VV and others failed.” This document is in English. (sic)
The report also explained the process of the attacks, using the delivery of one ‘additional file of interest’ “mohila meeting jan.pdf” as an example of how the RAT would launch itself automatically on start up, as explained in Caravan Report II, and allow the attacker to directly control the command line. The command history also contains a tell-tale syntax error, which the report highlights as “consistent with an attacker making a mistake and then correcting that mistake.”
5. Arsenal Consulting Report III – Surendra Gadling: Common Attacker, Common Techniques
21 June 2021: Arsenal was retained by Surendra Gadling’s defence team after he was provided access to a copy of his hard drive, which formed the basis of Arsenal’s forensic examination alongside his Yahoo email. The executive summary of the report is as follows:
Arsenal’s analysis in this case has revealed that Surendra Gadling’s computer was compromised for just over 20 months by the same attacker[13] identified in Reports I and II. The attacker responsible for compromising Mr. Gadling’s computer had extensive resources (including time) and it is obvious that their primary goals were surveillance and incriminating document delivery. Arsenal has effectively caught the attacker red-handed, based on remnants of their activity left behind in file system transactions, application execution data, and otherwise. It is important to note that Arsenal has also recovered communications with the attacker’s command and control server from Mr. Gadling’s computer. Arsenal has connected the same attacker to a significant malware infrastructure which was deployed over the course of approximately four years[14] to not only attack and compromise Mr. Gadling’s computer for 20 months, but to attack his co-defendants in the Bhima Koregaon case and defendants in other high-profile Indian cases as well. It should be noted that this is one of the most serious cases involving evidence tampering that Arsenal has ever encountered, based on various metrics which include the vast timespan between the delivery of the first and last incriminating documents on multiple defendants computers.
Surendra Gadling’s computer was compromised on 29th February 2016 after receiving a series of emails containing NetWire (the same RAT that was used to infect Rona Wilson’s system) and remained compromised till a complete Windows reinstallation on 2nd November 2017 effectively knocked the attacker off the system. The reinstallation took place 5 months before police seizure on 17th April 2018, the same day co-accused Rona Wilson’s devices were seized. The chain of events leading up to 2nd November 2017 as recovered by Arsenal is as follows:
- 12 February 2016: Gadling receives two emails containing NetWire in different packages, one from Harshal Lingayat at 9:13PM and the next from Prashant Rahi at 11:54PM. It is pointed out that by this time, the malware infrastructure has spread significantly in the network of targeted activists, leading to the compromise of their emails.
- 18 February 2016: Gadling receives another email containing the RAT, this time from the compromised email of Arun Ferreira, another co-accused.
- 29 February 2016: All three emails from the above three senders contained identical installation scripts for NetWire, one of which was run on the 29th and executed a series of commands leading to the opening of a decoy document and NetWire being launched and made persistent parallelly. The IP address of the C2 server that the malware connected to upon launching has been associated with two of the attacker’s hostnames crucial to the case, and listed in Report I.
- 29 February 2016 to 3 December 2016: As with Rona Wilson’s computer, Surendra Gadling’s computer was infected with multiple NetWires, with at least 6 having been customised by 3 December 2016, and four more possibly existing on the disk that could not be confirmed. These samples connected to the same C2 server as mentioned in (3) above with identical configuration as in the case of Rona Wilson.
- 5 March 2016 to 22 October 2017: As with Rona Wilson, NetWire logs recovered by Arsenal revealed severe monitoring and surveillance of Gadling’s digital activity, including browsing websites, submitting passwords, composing emails, and editing documents. In this case as well the attacker made use of various additional tools to synchronise Gadling’s disk and attached drives (at least 15 of them, containing over 30,000 files) to their C2 server.
- 4 December 2016 to 22 October 2017: A hidden folder “Material” (similar to “Rbackup” on Rona Wilson’s computer) was created through NetWire on the 4 December 2016. It is into this folder that the 14 files relevant to the case against Surendra Gadling are delivered via NetWire and by no other means over the course of the next 10 months. The method of delivery followed the modus operandi established during the investigation of Rona Wilson’s devices: .rar archives are delivered, a more recent version of WinRAR is temporarily deployed to unpack them, and the archives and executables are deleted. As in the case of Wilson, this version of WinRAR used is different from the one present on Gadling’s system, which has a history of legitimate use, and was deployed specifically for these tasks by the attacker. Again, analysis of Object Identifiers revealed that none of these 14 files was ever interacted with in any legitimate way or that the folder they were contained in was ever opened. Following are the 14 files in chronological order of delivery.
- File 1 – Please read.txt: Created on 4 January 2017 (10:49:16.216 IST) via NetWire attack. Summarised by Arsenal as follows:
Alleged letter from “Prakash” to “com. Surendra.” Mentions sending important material including guidelines and decisions accepted in the last “ERB” meeting. Also mentions consolidating all bolshevik forces and organizing something on 6th April to remember the heroic and bold actions of the PLGA against the reactionary forces. This document is in English. (sic)
-
- File 2 – Dear Surendra.docx: Created on 20 January 2017 (12:32:57.555 IST) via NetWire attack. Summarised by Arsenal as follows:
Alleged letter to “Surendra.” Mentions not being able to meet as planned, legal defense work, and concern about “Com. Murgan.” Praises “Arun” and “Vernon” for their efforts to organize students. Mentions “Mahesh” and “Nandu” “have reached to us safely” and that some “PR’s” (professional revolutionaries) from “TISS” are also expected. Asks for an update about an upcoming IAPL conference and concludes by saying “… I will be reachable through com. Manoj.” This document is in English. (sic)
-
- File 3 – Prakash_MZ.pdf: Created on 20 February 2017 (22:52:30.336 IST) via NetWire attack. Summarised by Arsenal as follows:
Alleged letter from “Surendra” to “Com. Prakash.” Mentions that “Varavara Rao” has sent funds that Gadling is waiting for, and without that funding the fact finding team will not able to do their work. Discusses an “operation” involving comrades from the jungle and the supply of money and materials for guerilla war. Also mentions “Saibaba’s” release as a priority. This document is in Hindi. (sic)
-
- File 4 – Letter_MSZC.pdf: Created on 20 February 2017 (22:52:30.518 IST) via NetWire attack mere milliseconds after File 3. Summarised by Arsenal as follows:
Alleged letter from “Milind.” Mentions that under the guidance of “Com. Varavara Rao” and “Com. Surendra Gadling”, the attacks made in Gadchiroli and Chhattisgarh were successful and recognized all over India. Describes funds being sent by “Com. Varavara Rao” to “Com. Surendra” to make available to the letter recipient. Also mentions that “Com. Varavara Rao” and “Com. Surendra” will give guidance to the letter recipient at an upcoming meeting in Nagpur. This document is in Hindi. (sic)
-
- File 5 – Ltr_CC_2_P.pdf: Created on 08 March 2017 (21:33:10.636 IST) via NetWire attack. Summarised by Arsenal as follows:
Alleged letter from “dada” (brother in Hindi/Bengali) to “Prashant” on February 10, 2017 on Maoist party Central Committee letter head. Mentions state repression and problems in communicating. Requests that legal work be sped up for particular jailed activists. Shares concerns about “Sai” and the present situation of “CRPP” in Delhi. Also requests that “SG” call on the “safe number” on particular days and times before the “final hearing”. This document is in English. (sic)
-
- File 6 – Ltr_2_SG.pdf: Created on 14 March 2017 (22:13:05.421 IST) via NetWire attack. Summarised by Arsenal as follows:
Alleged letter from “Com. Varavara” to “Com. Surendra.” Mentions that his assurance to the organization has failed regarding Saibaba’s case, causing immense loss to the organization including fissures in urban cadre forces. Also mentions that the organization is angry with Surendra about a lack of funding. Directs Surendra to compensate the organization immediately, and to contact Chhattisgarh comrades to work towards breaking the confidence of the enemy. This document is in Hindi.
-
- File 7 – Reply_2_VV.pdf: Created on 21 March 2017 (12:40:16.062 IST) via NetWire attack. Summarised by Arsenal as follows:
Alleged letter from “Surendra” to “Com. Varavara Rao.” Mentions that he tried his best to keep his assurances regarding “Saibaba’s” case but judiciary sided with the enemy. Also mentions being in touch with senior CC comrades about an operation planned by “Varavara Rao.” Discusses a successful operation in Gadchirolli and lists places where deployment of enemy forces is lower and suitable for ambush. This document is in Hindi. (sic)
-
- File 8 – MoM-Final.pdf: Created on 16 April 2017 (23:29:53.150 IST) via NetWire attack. Summarised by Arsenal as follows:
Alleged letter from “Sudha” to “Prakash.” Includes minutes of an IAPL meeting held in Nagpur. Minutes mention offering urban cadres “packages” so that they don’t stay afraid after Saibaba’s arrest and “Com. Surendra” and “Stan Swamy” not being able to provide money. This document is in English.
-
- File 9 – Ltr_2704.pdf: Created on 05 May 2017 (14:45:52.540 IST) via NetWire attack. Summarised by Arsenal as follows:
Alleged letter from Comrade Surendra to Comrade Prakash outlining Surendra’s meeting on April 22, 2017 with a respected comrade from Chhatisgarh in Delhi, and handing over funds transferred via hawala for Bastar and Maharashtra “operations.” This document is in Hindi.
-
- File 10 – Dear Sudarshan da.pdf: Created on 15 May 2017 (14:22:48.842 IST) via NetWire attack. Summarised by Arsenal as follows:
Alleged letter from “SG” to “Sudarshan da.” Mentions interaction with “kishan da” regarding enemy movements in Bastar and other areas of interest. Mentions that “Com. Ramchandra” has been tasked with identifying soft targets. Discusses upcoming IAPL all India congress and Ambedkar Periyar Study Circle, and people dealing with IAPL-related matters. This document is in English. (sic)
-
- File 11 – CC_letter-08Jun.pdf: Created on 10 July 2017 (13:38:17.708 IST) via NetWire attack. Summarised by Arsenal as follows:
Alleged letter from “comrade M.” to “comrade Surendra.” The first part of this letter refers to complaints from the Delhi Women cadre and the party leadership taking gender bias, patriarchy, and authoritarian tendencies within the “MO leadership” seriously. The second part of this letter refers to setting up a day-long program on the theme of the 50th anniversary of the Naxalbari movement. This document is in English.
-
- File 12 – Ltr_16July17.pdf: Created on 22 July 2017 (13:45:33.017 IST) via NetWire attack. Summarised by Arsenal as follows:
Alleged letter from “Prakash” to “Surendra.” Mentions visiting Chennai to join “Com. Arun.” and that the party is taking measures to get jailed comrade “Adv. Murugan” released. Asks “Surendra” to speak with Adv to find youths to motivate them to become “PR’s” and for timely updates on “Com. Saibaba’s” case. This document is in English.
-
- File 13 – Dear Sudarshan da..pdf: (Not to be confused with file 10.) Created on 08 September 2017 (12:34:55.434 IST) via NetWire attack. Summarised by Arsenal as follows:
Alleged letter from “SG” to “Sudarshan da.” Mentions incorporating “R.Bhalla” into the “EC” in the upcoming IAPL meet and providing legal relief to imprisoned “Adv. Murugan.” Urges the collection of funds for IAPL work. This document is in English.
-
- File 14 – Ltr_2_SG-250917.pdf: Created on 30 September 2017 (22:43:53.771 IST) via NetWire attack. Summarised by Arsenal as follows:
Alleged letter from “Com. Prakash” to “comrade Surendra.” Mentions overwhelming enemy forces around “MH/CHH border.” Asks whether Surendra has received two pgp files containing action plan made with observations from senior leaders including “com. G.” Discusses strengthening student protests through “DUSU”, “JNUSU”, “APSC”, “AISF”, and “NSUI.” Concludes by mentioning getting assistance from Congress leaders, providing a phone number for “our friend”, and asking to be informed about “Sai” and “other senior comrades.” This document is in English.
- 22 July 2017: The attacker simultaneously accesses Rona Wilson’s and Surendra Gadling’s systems, both of which have been compromised by them at this point, and delivers one identical file “CC –Financial Policy.docx” to both of them, first to Wilson’s computer, then to Gadling’s, after which it is deleted from Wilson’s computer.
6. Arsenal Consulting Report IV – Rona Wilson: Pegasus and the Government’s Involvement
18 August 2021: In its fourth report relating to the instant case, and third based on the hard disk of Rona Wilson, the agency looked specifically for indicators of the infamous NSO Group spyware ‘Pegasus’ following Amnesty International and Citizen Lab’s report revealing those among the ‘BK16’ to be among those in a leaked list of targets. The methodology used in the report followed that of Amnesty International. The report confirmed the presence of Pegasus Indicators (reflecting attacks) on Wilson’s drive as well as a successful infection of his phone since at least 5 July 2017. Unlike Reports I and II, this one speaks about having examined only the hard disk and not the Cruzer blade. The executive summary of the report is as follows:
Arsenal found Pegasus Indicators on the Windows volume of Mr. Wilson’s computer in two iTunes backups from an iPhone 6s, serial C7JQL293GRY9 (hereafter, “Mr. Wilson’s iPhone 6s”). Timestamps associated with these indicators span from July 5, 2017 to April 10, 2018. According to the Amnesty International article “Forensic Methodology Report: How to catch NSO Group’s Pegasus”, the indicators found by Arsenal reflect not only Pegasus attacks, but successful Pegasus infection of Mr. Wilson’s iPhone 6s. It is important to note that during this entire timespan of Pegasus attacks and infection of Mr. Wilson’s iPhone 6s, the attacker identified in Arsenal Reports I, II, and III was using the NetWire RAT (Remote Access Trojan) on Mr. Wilson’s computer for purposes of both surveillance and incriminating document delivery. (sic)
7. Arsenal Consulting Report V – Stan Swamy: How Far Do the Roots Go Down?
11 December 2022: The latest and lengthiest of Arsenal’s reports was produced after Arsenal was retained by the defence team for the late Stan Swamy or Fr. Swamy), and was based on analysis of a copy of his hard drive, which was seized along with his computer by the Pune police dept. on 12 June 2019. The executive summary of the report is as follows:
Arsenal’s analysis in this case has revealed that Stanislaus Lourduswamy’s computer was compromised by the same attacker[15] identified in Reports I, II, and III over the course of three distinct campaigns, beginning on October 19, 2014 and ending upon the seizure of his computer by Pune police department on June 12, 2019. The attacker responsible for compromising Fr. Swamy’s computer had extensive resources (including time) and it is obvious that their primary goals were surveillance and incriminating document delivery. Arsenal has effectively caught the attacker red-handed (yet again), based on remnants of their activity left behind in file system transactions, application execution data, and otherwise. It is important to note that Arsenal has also recovered multiple types of communications with the attacker’s command and control server from Windows hibernation data on Fr. Swamy’s computer. Arsenal has connected the same attacker to a significant malware infrastructure’ which we now know was deployed over the course of over six years[16] to not only attack and compromise Fr. Swamy’s computer during the aforementioned timespan, but to attack his co-defendants in the Bhima Koregaon case and defendants in other high-profile Indian cases as well. It should be noted that this is one of the most serious cases involving evidence tampering that Arsenal has ever encountered, based on various metrics which include the vast timespan between the delivery of the first and last incriminating documents on multiple defendants computers. Arsenal’s findings in this report (and all of our others) can be replicated by competent digital forensics practitioners with access to the same electronic evidence. (sic)
Stan Swamy’s computer was first compromised on 19 October 2014, through a NetWire executable identical to those mailed to co-defendant Rona Wilson, on the 16th and 28th of November in the same year. Onwards, the system remained compromised for a period of 56 months until the seizure of his devices in 2019. In this period, Fr. Swamy was the victim of three separate NetWire campaigns, one of which was identical to those deployed against co-defendants Rona Wilson and Surendra Gadling. The chain of events, as reconstructed by Arsenal during this period, is as follows:
- 19 October 2014: Stan Swamy’s computer is compromised after an unwitting execution of a NetWire sample, embedded in a weaponised MS Word document, marking the beginning of the first campaign, called “itfuturisticspvt“. One sample launched and configured under this campaign was found by Arsenal. How the document was delivered to the system is not mentioned.
- 1 August 2016: The 2nd NetWire campaign, called “atlaswebportal” begins. This campaign was also used against co-defendants Rona Wilson and Surendra Gadling, and even had the same configuration (server, port and password). Four NetWire samples launched and configured under this campaign were found by Arsenal.
- 20 April 2019: The 3rd NetWire campaign, called “researchplanet” begins. Seven NetWire samples launched and configured under this campaign were found by Arsenal. This means that at least twelve RATs were deployed in Fr. Swamy’s system over the course of these three campaigns.
- 21 July 2015 to 11 June 2019: Fr. Swamy’s activity was heavily monitored through the Trojans, including browsing websites, submitting passwords, composing emails, and editing documents. The passwords stolen during this period also helped the attacker maintain persistence in Fr. Swamy’s emails, as well as in the cases of his co-defendants.
- 2 August 2016 to 9 June 2019: Following the modus operandi seen in the compromise of Rona Wilson and Surendra Gadling’s computers in reports I and III, Fr. Swamy’s disk and removable devices were synchronised with the attacker’s C2 servers using an open source file transfer client for Windows. At least 13 removable storage devices were synchronised in this manner, with over 24,000 files. Among the many scripts run by the attacker for this, each heavily obfuscated with “noise” which Arsenal stripped in their investigation, was one which contained the phrase “Now we can run XCOPY and fuck the machine!” The report highlights that this phrase had not been found on the other defendants’ devices. Another noteworthy observation was the customisation of the attacker’s infrastructure (such as their usernames, passwords, and folder names) to match the victim’s background, for e.g. “stan@socialstudies.zapto.org=41” specifically for Stan Swamy’s computer.
- 20 July 2017 to 5 June 2019: Following the modus operandi encountered in reports I, II and III, a hidden folder named ‘mydata’ (see ‘Material‘ on Surendra Gadling’s computer and ‘Rbackup‘ on Rona Wilson’s) was created through a NetWire attack on 20 July 2017. It is to this folder that ‘terrorism related documents’ were eventually delivered over the course of two subsequent NetWire campaigns, following the same methodology used in his two co-defendant’s cases: files were delivered first as .rar archives which were unpacked by a version of WinRAR temporarily deployed for this specific task, after which it was deleted along with the .rar archives. Again, the version of WinRAR present on the system with a history of legitimate use was different from the one used to unpack the planted files. A total of 57 such files were delivered to Fr. Swamy’s system in this manner, including deployed executables, folders, archives, .xlsx, .doc, .docx, and .pdf files. Several of these, the last four in particular, apart from the archives and WinRAR executables that the attacker normally deleted after use, were also delivered, deleted, redelivered, and thus modified by the attacker. Barring those, there were 44 documents (.xlsx, .doc, .docx, and .pdf) on Fr. Swamy’s system at time of seizure delivered to the hidden folder through NetWire, which were the ‘terrorism related documents‘ that he was accused of possessing. This is a significantly larger number than in the cases of his co-defendants and corresponds to the longer period of his system’s compromise and proportional severity of the attack against Fr. Swamy. As in the case of Rona Wilson, certain documents (listed below) were created using a version of MS Word not available on Fr. Swamy’s computer. Arsenal discovered NetWire “stacks” (memory-based remnants of the Trojan’s use) authoritatively demonstrating that the files were delivered using NetWire. Analysis of Object Identifiers showed that none of these files was ever interacted with in any legitimate way. A few notable documents are summarised below in chronological order of delivery:
- Notable Document 1 – Dear Vijayan dada.pdf: Created on 07/20/2017 (15:31:56.532 IST) via NetWire attack, using MS Word 2010. Purportedly authored by Fr. Swamy.
- Notable Document 2 – Dear Vijayan dada 05.10.17.pdf: Created on 10/12/2017 (14:44:22.498 IST) via NetWire attack, using MS Word 2010. Purportedly authored by Fr. Swamy. The document concluded with the phrase, “On the ground level there must be some action from your side to capture senior leaders of ruling BUP in the state and demand that the oppressive laws be done with.”
- Notable Document 3 – PLGA Status at Unity Congress.pdf: Created on 05/02/2019 10:49:04.165 IST) via NetWire attack. The document contains details about Peoples (sic) Liberation Guerrilla Army units, including numbers of personnel and types of available weapons in various Indian states.
- Notable Document 4 – Weeping Salandi – A PUCL Report on Communal Violence in Bhadrak, Odisha.pdf: Created on 05/05/2019 (14:37:13.674 IST) via NetWire attack. This file along with its contents was accessed through analysis of memory-based remnants of NetWire activity found in ‘buffers’. It is one of four files discovered this way.
- Notable Document 5 – PERSECUTED PRISONERS SOLIDARITY COMMITTEE.docx: Created on 05/05/2019 14:43:57.791 IST) via NetWire attack. This file was uploaded before “Inheritors of Naxalbari.docx” and after “Weeping Salandi – A PUCL Report on Communal Violence in Bhadrak, Odisha.pdf’, but none of its contents remained in the ‘buffer’ where it was accessed by Arsenal as its size was smaller than “Inheritors of Naxalbari.docx” and was thus completely overwritten. It is one of four files discovered through analysis of such ‘buffers’.
- Notable Document 6 – Inheritors of Naxalbari.docx: Created on 05/05/2019 (15:00:30.476 IST) via NetWire attack.
- Notable Document 7 – 15-5-17 Minutes.docx: Created on 05/05/2019 (16:27:37.649 IST) via NetWire attack.
The remaining 37 files were named: ‘2NS 0n Burning Forest_H.doc.pdf’, ‘2017-09-06_CC Stmnt Condemning Gauri Lankesh’s Assassination By BHF doc.pdf’, ‘2017-09-07_DKSZC Stmnt_Appeal 2 Sarv Adivasi and Bang Samaj_For Audio.doc.pdf’, ‘2017-9-26_CC stmt Eng on Rohingya.pdf’, ‘Eng_Ad_CC Message_13th Anniversary On Sept 21 2017.pdf’, ‘CMC letter on geedam.pdf’, ‘Concealment.pdf’, ‘Essential Underground Handbook (P M L Publishing).pdf’, ‘Secrets of RAW_v.k singh.pdf’, ‘YAESU VX-110 Operating manual.pdf’, ‘Dear Father Stan.docx’, ‘Gadchiroli Draft.docx’, subfolder ‘ILPS cananda’ (containing ‘canada.docx’, ‘18670937_$19227114867928_2573447111373526863_n.jpg’, ‘18671270_$19227054867934_3104159175336557907_n.jpg’, ‘18739731_51921167820280S_4997021182425215365_n.jpg’, ‘18767694_519227191534587_7182052400932737369_n.jpg’ and ‘18813678_519226461534660_949292694280721616_n.jpg’), ‘Documents accepted in the 2nd Conference of MLRO.pdf’, ‘The Strategy of the Indian Revolution MCC_Book pdf, WUCom Letter to ACs_2014.pdf’, ‘Mini manual of the urban guerilla2.pdf’, ‘Circular on Marriage, Family and Sex.doc’, ‘FinalPor-Eng.doc’, ‘Strategy and Tacties-E_May.doc’, ‘PB Tech CIR-H_10.Sep.pdf’, ‘Party Constiiion Hindi.pdf, Ltr2 Hyd 25Jan.pdf’, ‘For foreign delegates.pdf’, ‘Lr to com.P-Aug17.pdf’, ‘Plan for evaluation of LM-converted.pdf’, ‘Rome visit Ltr to CSAs TF-SJESS0-May’19.doc’, ‘Zonal, State and National Workshops(1).xlsx’, ‘MISEREOR (draft Proposal (1).docx’, ‘LM Report.doc’, ‘Rosemary Nag (1).pdf’, ‘Lr_toSCM-2105.pdf’
- 11 June 2019: The attacker began to perform an extensive clean-up of their malicious activities using NetWire, including crude anti-forensic activity, which was abruptly interrupted by a manual shutdown legitimately initiated by Fr. Swamy himself at 21:01:28 IST. Arsenal has highlighted the clean-up as “both unique and extremely suspicious given the computer’s imminent seizure” the following day on 12 June 2019. The clean-up included:
- Deletion of NetWire logs, scheduled attacks and malicious tasks, NetWire wrappers, scripts, surveillance resources such as a hidden staging area from which files from Fr. Swamy’s computer were synchronised with the attacker’s C2 server, and other tools including several NetWires.
- Creation of “noise”.
- Renaming of suspicious malicious folders to unsuspicious names such as “Desktop” and “OperaBak”.
The deletion of surveillance activity included one massive deletion of 14,313 files from the hidden staging area through a command “del /f /q /s” which has been highlighted by Arsenal for not only being a significant deletion but for being a “forceful, quiet and recursive” one. A similarly desperate command was used for the creation of “noise” in two folders where malicious activity had taken place, where files were copied using “copy /s /c /h /r /y“: recursively (/s), ignoring errors (/c), with hidden and system files (/h), with read-only files (/r), and suppressing any prompts regarding overwriting existing files (/y). Again, it should be noted that this activity was taking place the night immediately prior to the seizure of the device, and was abruptly interrupted by manual shutdown, before the attacker could send the NetWire “a1” control command for removing itself.
8. SentinelOne Report – A Decade of ModifiedElephant
9 February 2022: A report by another US based firm, AI-oriented security firm SentinelOne’s SentinelLabs, titled ‘ModifiedElephant APT and a Decade of Fabricating Evidence‘ and authored by Tom Hegel, that tied together all the attacks and operational history of the common attacker identified by Arsenal, was released. “Activists, human rights defenders, journalists, academics, and law professionals in India are those most highly targeted. Notable targets include individuals associated with the Bhima Koregaon case,” the report said.
This threat actor (APT stands for ‘Advanced Persistent Threat‘) was named “ModifiedElephant“, and following the indicators of their activity already identified by Arsenal, Sentinel was able to uncover an even longer history of activity—at least 10 years and counting at time of publication in 2022. As of February 2025, ModifiedElephant is still active. The executive summary of the report is as follows:
- Our research attributes a decade of activity to a threat actor we call ModifiedElephant.
- ModifiedElephant is responsible for targeted attacks on human rights activists, human rights defenders, academics, and lawyers across India with the objective of planting incriminating digital evidence.
- ModifiedElephant has been operating since at least 2012, and has repeatedly targeted specific individuals.
- ModifiedElephant operates through the use of commercially available remote access trojans (RATs) and has potential ties to the commercial surveillance industry.
- The threat actor uses spearphishing with malicious documents to deliver malware, such as NetWire, DarkComet, and simple keyloggers with infrastructure overlaps that allow us to connect long periods of previously unattributed malicious activity.
Sentinel worked towards and succeeded in expanding the modus operandi of ModifiedElephant, as had been clearly established in the first three Arsenal reports alongside other reportage:
- RAT Infection via Spearphishing: Use of commercial rats like NetWire/DarkComet, free email domains such as Gmail and Yahoo.
- Long term surveillance using open source tools: WinSCP for C2 synchronisation.
- Planting of fabricated incriminating evidence: .rar archives unpacked by temporarily deployed UnRAR into nested hidden folders.
- Clean-up/continued malicious activity leading up to the time of seizure of devices by state agencies: Crude/desperate anti-forensic activity, deletions, cancellations of scheduled tasks, or deliveries of important incriminating documents, before the seizure.
While the objective of ModifiedElephant’s attacks remained long term surveillance culminating in the planting of fabricated evidence leading up to and coordinated with the target’s arrest as analysed by previous investigators, Sentinel made significant expansions on their history of activity (traced back all the way to 2012), in their surveillance techniques and choice of malware. For instance, the report found that even before making their foray into commercially available RATs, ModifiedElephant made use of crude keylogging techniques to spy on targets, and that in addition to NetWire and DarkComet, also made use of the GM Bot and an unidentified Android Trojan delivered as APK (application) files described as an ‘ideal low-cost mobile surveillance toolkit.’
One of the most noteworthy conclusions of the report is the confirmation of a speculation that has remained consistent throughout the Arsenal reports: the surprisingly unsophisticated nature of ModifiedElephant’s attacks. The malware infrastructure used most often by the attacker was described as ‘unsophisticated and downright mundane.’ Their longer-lived techniques, such as the above-mentioned keylogging, have been described as extremely brittle to the point of being dysfunctional, technically unimpressive and likely to have been plagiarised. Following is an excerpt describing ModifiedElephant’s ‘Incubator keylogger’ (so named because of a term used in its code):
[The keyloggers], packed at delivery, are written in Visual Basic and are not the least bit technically impressive. Moreover, they’re built in such a brittle fashion that they no longer function. The overall structure of the keylogger is fairly similar to code openly shared on Italian hacking forums in 2012. In some ways, the Incubator keylogger is far more brittle than the code referenced above as it relies on specific web content to function.
The report also covered ModifiedElephant’s relations to other threat actors and malware infrastructures, including another Advanced Persistent Threat actor within India, called SideWinder, that operated alongside it with overlapping durations of activity as well as overlapping targets (both limited to phishing emails). Between February 2013 and January 2014, Rona Wilson was targeted by such emails by SideWinder. Pegasus, FinFisher, and Operation Hangover were also connected to the ModifiedElephant malware infrastructure.
9. The Wired – The Thrice Verified Link to Shivaji Pawar
6 June 2022: US based Tech magazine WIRED releases a report titled, “Police Linked to Hacking Campaign to Frame Indian Activists,” in reference to ModifiedElephant’s attacks against those arrested in the Bhima Koregaon/Elgar Parishad case. The report begins with an anonymous account by an employee of an unnamed email service provider, who confirmed that a recovery email and phone number were added to the accounts of Rona Wilson, Varavara Rao and Hany Babu at the time of compromise: a backway for the hacker to regain access to the systems and the mails. These recovery contacts belonged to an IPS officer who would later be named by SentinelOne’s Juan Andres Guerrero-Saade, along with Tom Hegel, at the upcoming Black Hat security conference—Shivaji Pawar!
These accounts, exclusively given to WIRED on the condition of anonymity, are then twice more confirmed by named sources: Scott Railton at the Citizen Lab (who previously collaborated with Amnesty International on their report on the hacking nexus targeting Bhima Koregaon defendants), and security researcher Zeshan Aziz.
10. KrebsonSecurity – The End of NetWire and a Lead to ModifiedElephant
9th March 2023: As per a report by the independent cybersecurity news & investigation website, KrebsonSecurity, the US FBI seized the domain ‘worldwiredlabs[.]com’ for the distribution of NetWire, after a Croatian national was arrested for allegedly administering it, & a computer server was seized in Switzerland for allegedly being in use for the same. None of the three authorities provided any information about the accused or the basis of his arrest, KrebsonSecurity’s investigation nevertheless covered the case in based on both information available in the public domain, interviews with the accused, as well detailed digital sleuthing.
References/Links
- https://caravanmagazine.in/law/did-pune-police-tamper-evidence-against-bhima-koregaon-accused
- https://caravanmagazine.in/politics/bhima-koregaon-case-rona-wilson-hard-disk-malware-remote-access
- https://www.newslaundry.com/2021/01/02/bhima-koregaon-case-three-years-of-legal-and-rights-violations
- https://krebsonsecurity.com/2023/03/whos-behind-the-netwire-remote-access-trojan/
- https://drive.google.com/drive/folders/1QoonWsBbpWiJFaIl2zgLN6l0rxezNHHa?ref=static.internetfreedom.in
- http://books.ms/main/B3FC3CA9814A81AE801C34AC123DAB88
- https://www.satp.org/south-asia-intelligence-review-Volume-17-No-10
- https://thewire.in/politics/modi-assassination-plot-letter-danger-democracy
- https://www.amnesty.org/en/latest/research/2020/06/india-human-rights-defenders-targeted-by-a-coordinated-spyware-operation/
- https://www.ripe.net/ripe/mail/archives/anti-abuse-wg/2016-July/003450.html
- https://www.amnesty.org/en/latest/research/2021/07/forensic-methodology-report-how-to-catch-nso-groups-pegasus/
- https://assets.sentinelone.com/sentinellabs-apt/modified-elephant-apt
- https://securityintelligence.com/gm-bot-alive-upgraded-now-android-m/
- https://www.virustotal.com/gui/file/4dbb14ff2836733b34594956c4234d2a54c04257710dd31a0884b1926d35d7bc
- https://www.theverge.com/2015/1/21/7861645/finfisher-spyware-let-bahrain-government-hack-political-activist
- https://web.archive.org/web/20210226131047/https://paper.seebug.org/papers/APT/APT_CyberCriminal_Campagin/2013/NS-Unveiling-an-Indian-Cyberattack-Infrastructure_FINAL_Web.pdf
[1] Only a small component of the gross procedural violations made during the entire investigative process, including but not limited to the illegal nature of the raids themselves, which were conducted against twice denied warrant applications. This and other violations had been compiled by Prateek Goyal in a report for Newslaundry in January 2021.
[2] In March 2023, a Croatian national was arrested for distributing the RAT, and its website was seized by the US FBI. Though charges have not been proved (or even framed) against the accused in the instant case so far, it is through this website that NetWire was sold for 11 years between its creation in 2012 and its seizure in 2023, and is likely where Rona Wilson, Surendra Gadling and Stan Swamy’s common attacker, the notorious ModifiedElephant, purchased it from as well. SentinelOne’s report on ModifiedElephant’s history of attacks suggested potential ties between the APT and the commercial surveillance industry.
[3] “The incriminating documents were delivered to a hidden folder on Mr. Wilson’s computer by NetWire and
not by other means.” (p. 7)
[4] “One method that can be used to assist in determining whether a particular document has ever been opened on a particular computer is to review the NTFS file system’s “object identifier” (a/k/a $OBJECT_ID) attributes for that document. Object identifiers are normally assigned to documents when they are either created or first opened. In this case, none of the top ten documents have object identifiers.” (p. 7)
[5] This is hard evidence of technical impossibility, and should be viewed in addition to the pre-existing arguments for the implausibility of Wilson or any of his co-accused having been either the authors or intended recipients of the letter based on its linguistic analysis: Alpa Shah in her book The Incarcerations (p. 286-288) analysed the language and structure of the letter and highlighted notable inconsistencies both within its internal language and in its use of real names of people and weapons, both gross violations of standard Maoist practice of using exclusively codenames for correspondence; Dr. Ajai Sahni in his report Urban Maoist Fakery for the South Asia Terrorism Portal said, the letters have all the hallmarks of mischievous fabrication… It is unlikely that these letters (yet to be placed before the courts, but widely circulated in the media) will stand up to judicial scrutiny either. Crucially, the language, content and character of this purported correspondence militates against everything that is known about the Maoists.’ The logico-linguistic analysis of the letters by various experts indicates fabrication, in addition to the NetWire implantation discovered in Arsenal’s investigation.
[6] Corrected to at least six years in the fifth Arsenal report, and since at least 2012 as per the SentinelOne ModifiedElephant investigation.
[7] Amnesty International Report.
[8] Access to Rao’s seized hard drive can clarify how his email was compromised.
[9] Also used in the case of the ‘top 10’ along with various other cyber tools.
[10]12 files including the .rar file that contained 10 more.
[11] The files were located in an AVCHDCoder folder, which should only contain data related to the use of the eponymous program, used for video file conversion. Arsenal highlighted this to be ‘suspicious’.
[12] It should be noted that none of the deliveries from this point onward were ever unpacked, until the tenth and final ‘top ten most incriminating document’, Ltr_2_Anand_E.pdf was created on 6th April 2018.
[13] Later termed ModifiedElephant in SentinelOne’s 2022 report.
[14] Corrected to at least six years in the fifth Arsenal report, and since at least 2012 as per the SentinelOne report.
[15] Earlier termed the ModifiedElephant in Sentinel’s report published February the same year.
[16] Since at least 2012 as per SentinelOne’s report.
A complete chronology of the seven-year-long cyberattack (and it’s slow, horrific unravelling) carried out by the same threat actor against 16 human rights activists, who were resultantly incarcerated without trial under the UAPA for the alleged orchestration of the Bhima Koregaon violence at the start of 2018 and a made up plot to assassinate the prime minister of India. Christened by security firm Sentinel in 2022 after a series of tech investigations starting in 2019 with the discovery of a Trojan horse on researcher Rona Wilson’s seized system, the notorious ModifiedElephant has been targeting activists and HRDs in India since at least 2012 using extremely rudimentary means of surveillance, remote access, and file delivery, and worked directly with the Pune police (using IPS officer Shivaji Pawar’s contact information as its backway into the hacked systems) to frame members of the BK16. Worse still, the Pune FSL also protected ModifiedElephant, omitting crucial and unmistakable evidence of what was not only an astoundingly severe hackjob, but also—importantly—an astoundingly sloppy one, from its reports of forensic analysis of the devices.
Activists who have been confirmed to have been hacked within the ModifiedElephant campaign against the BK16:
- Stanislaus Lourduswamy: 56 Months
- Varavara Rao: Unknown Duration
- Arun Ferreira: Unknown Duration
- Harshal Lingayat: Unknown Duration
- Prashant Rahi: Unknown Duration
- Rona Wilson: 22 Months
- Surendra Gadling: 20 Months
Basic timeline of ModifiedElephant’s operation:
- 2012: The beginnings of ModifiedElephant, NetWire: Using primitive keylogging techniques, often stolen from online hacking forums, ModifiedElephant mass-forwards spyware through phishing emails using free services like Google or Yahoo. An APT (Advanced Persistent Threat), ModifiedElephant exclusively targets activists, lawyers, journalists, academics and HRDs, particularly those working for Adivasi, Dalit or prisoner rights. The same year, a notorious malware, NetWire was a commercially available Remote Access Trojan or RAT sold between 2012 and 2023. It allows a hacker to take complete control of the victim’s system.
- 2013-14: Gadchiroli arrests take place: Lt. Prof. GN Saibaba, Lt. Pandu Narote, Hem Mishra, Mahesh Tirki, and Prashant Rahi are arrested for “alleged Maoist links” under the UAPA. The case, subject of widespread criticism due to human rights violations by the state, is largely based on illegally seized electronic evidence.
- 2014-19: Wide-scale use of NetWire RAT begins against Indian HRD nexus: ModifiedElephant successfully compromises Stan Swamy’s system using NetWire. Their malware infrastructure expands exponentially, spreading through the entire nexus of government critical intellectuals. Emails of compromised victims are further used to target their friends and confidants.
After the compromise of Stan Swamy’s system, Arun Ferreira, Prashant Rahi, and Harshal Lingayat’s email accounts are compromised leading to the compromise of Surendra Gadling’s system for 20 months. Additionally, Hany Babu’s email is also compromised. Varavara Rao’s email is compromised leading to the compromise of Rona Wilson’s system for 22 months.
The most extensive attacks are carried out against Swamy, Surendra Gadling, and Rona Wilson, each of whom advocated for the release of the Gadchiroli accused, and each of whom will be implicated in the Bhima Koregaon case between 2018-19 based on electronic evidence already planted on their systems beforehand. These include letters discussing alleged Naxal links and a “plot to assassinate Narendra Modi.” At the time of compromise, a recovery email and phone number are added to the hacked accounts of 3 targets: Wilson, Rao and Babu. Both the email and phone number, which served as a backway entry into the accounts in case the victims tried to change their passwords, belonged to an IPS officer named Shivaji Pawar, who would eventually be an investigating officer of the Pune police in the Bhima Koregaon case.
- 2017-18: Pegasus: Israel’s Pegasus spyware, sold to governments across the globe for military and state espionage, is used to attack Rona Wilson’s devices, successfully hacking his iPhone6. A data leak in 2020 revealed that Wilson was among hundreds of HRDs and intellectuals – the same group targeted by ModifiedElephant – targeted by a mass surveillance attack using Pegasus, leading to the investigation by Arsenal. Traces of Pegasus activity on Wilson’s iPhone6 are found between 5th July 2017 and 10th April 2018, ending just a week before the seizure of his devices by the Pune police.
- 2018-20: Elgar Parishad: Also known as the Bhima Koregaon case. Two FIRs are registered regarding the violence in the region, between a caste Hindu ‘saffron brigade’ and the Dalit-Bahujan population commemorating their ancestors’ martyrdom at the 1818 Battle of Koregaon Bhima. The first names BJP-allied Hindu-extremist leaders Milind Ekbote and Sambhaji Bhide as responsible for the violence. The second alleges a conspiracy by Dalit/left-allied intellectuals, leading to the arrest of 16 individuals who happen to be ModifiedElephant/Pegasus targeted HRDs commonly referred to as the ‘BK16’ between 6th June 2018 and 8th October 2020. 7 years later, one of them has died due to inhumane prison conditions, nine have been released on bail following extensive legal intervention, and six of them are still in jail.
- 2019-22: Discovery and Unravelling of ModifiedElephant Malware Infrastructure: In 2019, The Caravan publishes a report after receiving true copies of some incriminating documents on Surendra Gadling’s computer which reveal evidence of tampering, and suspicions of fabrication. In 2020, The Caravan publishes another report after receiving a true clone of Rona Wilson’s hard disk, making a shocking discovery on his system: a Remote Access Trojan horse – a RAT. Specifically, it was a NetWire; one of five installed on Wilson’s computer – a discovery that triggered a series of cyber forensic investigations by agencies across the globe over the next 2 years, discovering, unravelling and exposing the massive cyber conspiracy spearheaded by the state-supported actor named ModifiedElephant. 5 of these reports were published by Arsenal Consulting, one by SentinelLabs, referencing three reports by Amnesty International and University of Toronto’s The Citizen Lab.
The IPS officer’s connections to the ModifiedElephant campaign (mentioned earlier) are exposed in a 2022 report by Wired.
- 2023: NetWire Distribution Website Seized: The US FBI seizes the domain worldwiredlabs[.]com. A Croatian national is arrested for allegedly administering it, and a computer server is seized in Switzerland. None of the three authorities provided any information about the accused or the basis of his arrest, but an independent investigation by digital security firm, KrebsonSecurity, covered the case in detail.
- 2024: Acquittal of Gadchiroli Accused: Over 10 years after they were arrested, the Bombay High Court acquitted the 6 accused of having ‘Maoist links’ due to invalid prosecution sanctions, stock witnesses, and a complete absence of credible evidence. The electronic evidence and other documentary evidence against them was squarely dismissed on account of egregious procedural violations suggesting mala fide tampering and the planting of incriminating documents. Pandu Narote died of illness in custody, in 2023, and Saibaba just about a year later, on being released, both victims of jail tribulations.
Comparative analysis of the attacks against Stan Swamy, Surendra Gadling and Rona Wilson (herein termed ‘Arsenal Reviewed Attacks’)
| Criteria/Victim | Stan Swamy | Surendra Gadling | Rona Wilson |
| Start of Compromise | 19th October 2014 | 29th February 2016 | 13th June 2016 |
| End of Compromise | 12th June 2019 | 2nd November 2017 | 17th April 2018 |
| Duration (in months) | 55 months, 24 days | 20 months, 4 days | 22 months, 4 days |
| Date of Seizure | 12th June 2019 | 17th April 2018 | 17th April 2018 |
| Date of Seizure same as End of Compromise? | Yes | No | Yes |
| Number of NetWire RATs | 12 | 10 | 5 |
| Nature of Attack | Long-term Surveillance and Incriminating Document Delivery | Long-term Surveillance and Incriminating Document Delivery | Long-term Surveillance and Incriminating Document Delivery |
| Surveilled Data | Browsed websites, submitted passwords, composed emails, and edited documents. | Browsed websites, submitted passwords, composed emails, and edited documents. | Browsed websites, submitted passwords, composed emails, and edited documents. |
| Location of Document Delivery | Hidden folder named ‘mydata’ | Hidden folder named ‘Material’ | Hidden folder named ‘Rbackup’ |
| Location of stolen files | Synchronised C2 server | Synchronised C2 server | Synchronised C2 server |
1. Caravan Report I – Police Tampering Raises Suspicions
14 December 2019: Caravan published a report analysing documents of police procedure and metadata of incriminating files on Surendra Gadling’s computer, provided to him by the prosecution through the relevant court, showing evidence of tampering and suspicious activity: the alignment of the text of an incriminating document was changed while the computer was under police custody, and all incriminating files were cut and pasted from various locations into a single folder on the desktop—where the police claim to have discovered them—within a span of 1 minute and 48 seconds on 7 December 2017. It also highlighted the selective violation of cyber evidence procedure[1], specifically the failure to record hash values corresponding to devices at time of seizure, with reference to the only devices on which ‘incriminating files’ were later found. Another noted inconsistency is that the incriminating files have been intercepted in the form of saved documents instead of emails where there could have been third-party verifiability regarding and complete track of the authors and receivers of the files. This is especially relevant in view of the fact that the majority of files found on Gadling as well as two of his co-defendant’s devices—Rona Wilson and Stan Swamy—on the basis of which they are accused, as noted in the first, third and fifth Arsenal reports, are correspondence documents.
2. Caravan Report II – Discovery of a Trojan
12 March 2020: After receiving a copy of Wilson’s hard disk, which had been presented in court by the Pune Police and supplied to all the accused, Caravan published another report by editor Martand Kaushik and software engineer Anjaneya Sivan based on their forensic investigation of the drive. The investigation revealed the presence of a malware on Wilson’s system, Win32:Trojan-Gen, capable of gathering protected information such as usernames and passwords, general surveillance, and remote access. The lattermost qualifies it as a Remote Access Trojan, or RAT, later identified as the infamous NetWire[2] by Arsenal Consulting.
The examination also revealed evidence of a clean-up of metadata, such as software logs, Windows explorer history, as well as document access history, all of which could have been used to track the use of the incriminating files and in turn, exonerate the accused. Another important discrepancy was the version of MS Word on Wilson’s computer, Word 2007, while the incriminating PDF documents found on his computer, which he was also accused of having authored, were created in either Word 2010 or 2013. The report highlighted that these findings had been notably omitted from the reports of the Regional Forensic Science Laboratory (RFSL), Pune.
Based on these findings, The Caravan made several speculations which were conclusively confirmed by a US based forensic firm called Arsenal Consulting in a series of five reports beginning in early 2021:
- That the discovery of a RAT on Wilson’s disk indicated the possibility of the devices of his co-accused being compromised as well, including those of Surendra Gadling, and emphasised the prosecution’s unwillingness to provide a copy of the disk as an obstacle to confirming the same. This was confirmed in the third Arsenal report, revealing that Gadling’s computer had been compromised for just over 20 months by the same attacker using the same RAT as in the case of Rona Wilson.
- That the malware may have been delivered to Wilson’s computer through malicious email or messaging links, and since it launched itself automatically on every start up, had been active on the device since long before it was seized. This was confirmed in the first Arsenal report, and the date of first compromise was found to be 13 June 2016.
- That the 10 incriminating documents on Wilson’s computer, including the sensational letter discussing an alleged plot to assassinate the prime minister and an uncanny purchase of sophisticated arms and ammunition for the CPI (Maoist), may have been planted using the aforementioned malware. This was confirmed in the first Arsenal report[3].
- That the deletion of metadata may be indicative of an intentional clean-up of evidence of ‘mischief by an investigative agency’ and of external implantation of evidence, which would enable the exoneration of the accused if it could be proven that the files were never in fact used, opened, or modified by him. This was confirmed in the first Arsenal report via an analysis of Object Identifiers, which demonstrated that the incriminating files had indeed never been ‘interacted with in a legitimate way’[4].
- That any version of MS Word more recent than the 2007 version had never been installed on Wilson’s computer, the only one in his possession, suggesting that he could not have authored the files[5]. This was confirmed in the first Arsenal report through an ‘aggressive search’ of Windows Registry information from Volume Shadow Copies, unallocated space, and elsewhere.
3. Arsenal Consulting Report I – Rona Wilson: An Unbelievable Malware Infrastructure
8 February 2021: Arsenal Consulting was retained by Wilson’s defence team to further analyse the seized electronic evidence, including his computer hard disk and a removable Cruzer blade. The executive summary of the report by Mark Spencer stated the following:
Rona Wilson’s computer was compromised for just over 22 months. The attacker responsible for compromising Mr. Wilson’s computer had extensive resources (including time) and it is obvious that their primary goals were surveillance and incriminating document delivery. Arsenal has connected the same attacker to a significant malware infrastructure which has been deployed over the course of approximately four years[6] to not only attack and compromise Mr. Wilson’s computer for 22 months, but to attack his co-defendants in the Bhima Koregaon case and defendants in other high-profile Indian cases[7] as well. It should be noted that this is one of the most serious cases involving evidence tampering that Arsenal has ever encountered, based on various metrics which include the vast timespan between the delivery of the first and last incriminating documents.
In detail, the analysis confirmed The Caravan’s various speculations as listed above, and discovered 4 RATs on the system in addition to the one discovered by Caravan. The chain of events starting with the compromise of Wilson’s computer leading up to the delivery of the final incriminating document and seizure of devices is as follows:
- 13th June 2016: Wilson’s computer is compromised through malicious links to a C2 (‘command and control’) server sent using Varavara Rao’s compromised email[8], which leads to the installation of NetWire on his device.
- 27th April 2016 to 30th October 2016: Five NetWire samples are wrapped on Wilson’s system, two of which are obfuscated. Between the creation of the last sample and the seizure of Wilson’s devices on 17th April 2018, these samples are used to heavily monitor his device use: ranging from browser history, password entry, to even simply documents being typed. This is done by synchronising the disk and two attached devices to C2 servers, including the seized Cruzer blade, using various additional tools.
- 3rd November 2016: The folder ‘kbackup’ is remotely created, renamed to ‘Rbackup’, and set to ‘hidden’. This hidden folder is where the ‘top ten most incriminating files’ (hereafter also ‘incriminating document(s)’ or collectively the ‘top ten’) were eventually delivered via NetWire, along with various other documents from Wilson’s system which were copied into it. The latter act is described in the report as “consistent with an attacker better obscuring forged documents amongst ‘noise’.”
- 29th March 2017 to 28 January 2018: Nine of the ‘top ten’ are delivered to the hidden folder Rbackup. They are delivered in the form of .rar archives unpacked by a version of WinRAR specifically deployed for the purpose of the attack (both of which will later be deleted), different from another WinRAR present in the system, which has a history of legitimate use. Following are 9 of the ‘top ten’ documents in chronological order of delivery.
- Incriminating Document 1 – Ltr_2_RW.pdf: Created on 29 March 2017 (11:03:01 IST) via NetWire attack. Summarised by Arsenal as follows:
Alleged letter from “Prakash” to “Comrade” mentioning failure of support among the people and “Comrade H.B.” taking over present and future tasks of “RDF.” The letter ends by discussing outreach to students of DUSU/JNUSU and “… it is on the shoulders of these young revolutionaries the future People’s War will be fought.” This document is in English.
-
- Incriminating Document 2 – Ltr_1804_to_CC.pdf: Created on 20 April 2017 (00:13:41 IST) via NetWire attack. This is the most incriminating of the ‘top ten’, and contains the alleged plot to assassinate India’s Prime Minister Narendra Modi and the uncanny purchase of sophisticated arms and ammunition. Summarised by Arsenal as follows:
Alleged letter from Rona Wilson to “comrade Prakash” mentioning a meeting which resulted in a requirement for 80 million rupees (approximately 1 million US dollars) annually to obtain M4 carbines (rifles with short barrels) and 400,000 rounds of ammunition. The letter also mentions taking “… concrete steps to end Modi-raj… along the lines of another Rajiv Ghandi type incident.” This document is in English. (sic)
-
- Incriminating Document 3 – Ltr_2704.pdf: Created on 5 May 2017 (21:31:58 IST) via NetWire attack. Summarised by Arsenal as follows:
Alleged letter from Comrade Surendra to Comrade Prakash outlining Surendra’s meeting on April 22, 2017 with a respected comrade from Chhatisgarh in Delhi, and handing over funds transferred via hawala for Bastar and Maharashtra “operations.” This document is in Hindi. (sic)
-
- Incriminating Document 4 – Ltr_2_P-51117.pdf: Created on 25 December 2017 (22:30:39 IST) via NetWire attack. Summarised by Arsenal as follows:
Alleged letter from Comrade Surendra to Comrade Prakash outlining contact with a Comrade Hemu for some “A.P.T materials.” Also mentions Comrades JRC and Pervaiz, and establishing an “IAPL” organization in Kerala. This document is in Hindi.
-
- Incriminating Document 5 – Ltr_2312_to_CC.pdf: Created on 25 December 2017 (22:31:01 IST) via NetWire attack. Summarised by Arsenal as follows:
Alleged letter from Rona Wilson to “comrade Prakash” explaining a focus on efforts to better understand “fake encounters” from Gadchiroli and raising awareness of political murders of journalists. The letter also mentions efforts to address schools and colleges with information concerning mob lynching and political murders. This document is in English.
-
- Incriminating Document 6 – Ltr_2612_to_CC.pdf: Created on 27 December 2017 (21:30:37 IST) via NetWire attack. Summarised by Arsenal as follows:
Alleged letter from Rona Wilson to “comrade Prakash” mentioning a supplier in Nepal and getting the “… equipment ready on the ground.” This letter also mentions a pressing need to “inflict heavy damage on the enemy forces” and transporting the “equipment” disassembled and concealed amongst “heavy electronics appliances.” This document is in English.
-
- Incriminating Document 7 – Ltr_from_Com.M_022018.pdf: Created on 06 January 2018 (02:05:39 IST) via NetWire attack. Summarised by Arsenal as follows:
Alleged letter from “Com. M” to “Comrade Rona” mentioning “PGP material”, possibly sending “CC comrades” to meet Swedish delegates in London, and “Dalit sentiments are clearly against the Brahmin-centered agenda of BJP/RSS, this should be converted into large scale mobilization and chaos.” This document is in English.
-
- Incriminating Document 8 – CC_letter – 08Jun.pdf: Created on 21 January 2018 (14:16:05 IST) via NetWire attack. Summarised by Arsenal as follows:
Alleged letter from “comrade M.” to “comrade Surendra.” The first part of this letter refers to complaints from the Delhi Women cadre and the party leadership taking gender bias, patriarchy, and authoritarian tendencies within the “MO” leadership seriously. The second part of this letter refers to setting up a day-long program on the theme of the 50th anniversary of the Naxalbari movement. This document is in English.
-
- Incriminating Document 9 – Ltr_2_SG-27.1.2018.pdf: Created on 28 January 2018 (19:14:01 IST) via NetWire attack. Summarised by Arsenal as follows:
Alleged letter from “B.A.S.” to “comrade Surendra.” This letter describes various expenses and financial arrangements. It also mentions being sent a “… new young boy (who has been living a military life for a year)” and “Once you were to sit with him for the first time, the doctor agreed to send a boy for 6 months in the jungle.” This document is in English.
- 14th March 2018: Before the delivery of the tenth document, several nesting attempts, transfers, and creation of dummy folders and files are performed from the system to the seized Cruzer blade, activities described in the report as “consistent with an attacker realizing [traceability/visibility of their activity] and/or deciding to more deeply nest the forged documents so that the victim would not stumble upon them.” The names of the dummy files match those found in the folder from which the first NetWire sample was originally launched, suggesting a continuity in carrying out the change.
- 6th April 2018: The tenth and final of the ‘top 10 incriminating’ documents is delivered, which is as follows:
- Incriminating Document 10 – Ltr_2_Anand_E.pdf: Created on 6 April 2018 (00:00:57 IST) via NetWire attack. Summarised by Arsenal as follows:
Alleged letter from “Prakash” to “Comrade Anand” mentioning the “CC” leadership being pleased with “… the progress that you have made on the Dalit Campaign.” This letter also mentions “International campaigns can give more traction to domestic chaos” and coordination with international friends. This document is in English.
- 16 April 2018: The final changes were made to the hidden ‘Rbackup’ folder, a modification to the MFT or Master File Table made at 16:50:41 IST, just one day prior to the seizure of the devices.
In addition to painstakingly reconstructing this chain of events, the report also identified several indicators of compromise that were related to the same attacker, which matched with indicators found in forensic images of devices belonging to Wilson as well as his co-defendants. These indicators included seven hostnames, 25 C2 IP addresses, all belonging to the infamous VPS HostSailor, as well as several file names with corresponding hash values. Through these indicators, alongside catching the attacker red-handed in its second and third report respectively, Arsenal discovered that the attacker is connected to an extensive malware infrastructure, and has been part of multiple campaigns using NetWire and DarkComet. In 2022, this work would form the basis for an AI based security firm called SentinelOne to further investigate this attacker and malware infrastructure, successfully connecting them to a notorious threat actor within India, who they would name ‘ModifiedElephant APT (Advanced Persistent Threat), that specifically targeted human rights activists, lawyers and defenders using commercial RATs and consistent modus operandi with the primary objective of long term surveillance culminating in the planting of fabricated incriminating evidence. The report would find that the APT had been active since at least 2012.
4. Arsenal Consulting Report II – Rona Wilson: Unfinished Incrimination and Footprints All Over
27 March 2021: Building on the investigation of the first report, the second continued its analysis of Rona Wilson’s hard disk and removable Cruzer blade, focusing on the 24 ‘additional files of interest’ – hereafter also referred to as ‘file(s) of interest’ or collectively the ‘additional 24’ – used to build the charges against him and his co-accused, in addition to the ‘top 10 most incriminating documents’ that have been established above as planted, most probably fabricated, and never interacted with. The executive summary of the second report is as follows:
Arsenal has determined that there is no evidence of legitimate interaction with the additional files of interest on Mr. Wilson’s computer, and that 22 of the 24 of the files are directly connected to the attacker identified in Report I. Arsenal has also provided a “process tree” with this report which effectively caught the attacker red-handed, by revealing both how NetWire and a temporarily deployed UnRAR[9] (from WinRAR v4.20) were used to deliver an additional file of interest to a hidden folder on Mr. Wilson’s computer, also capturing a command-line syntax mistake (and quick correction) made by the attacker. Details regarding how Mr. Wilson’s computer was initially compromised, and the attacker’s malware infrastructure, can be found in Report I.
The report concluded that the 24 additional files, just like the top ten most incriminating documents, were never interacted with in any legitimate capacity, and all but two of them were delivered into the system via NetWire and no other means, into the same hidden folder ‘Rbackup’, and by the same attacker[10]. The remaining two had suspicious sources. The deliveries were made between 25 December 2017 and 2 March 2018. 7 of the files were also discovered on the Cruzer blade, transferred on the 14th of March 2018.
Out of the 24 files, two were identified to be the same file renamed about 14 hours after its delivery, and 10 were contained within a .rar file delivered on 11 February 2018 directly through NetWire, and were never unpacked on the system. So, in total, the 24 files of interest constitute only 13 distinct deliveries: 11 through NetWire, and 2 identified as ‘suspicious’[11]. The latter two were picsdk.rar: a RAR archive which appears to contain photographs of Maoist party PLGA guerrillas, and mobile.rar: RAR archive which appears to contain a photograph of Milind Teltumbde, created on 22 January 2018 (20:09:40 IST) and 01 February 2018 (19:30:45 IST) respectively.
The 13 NetWire deliveries (described below as ‘Deliveries 1-11’) to Rbackup, including the .rar archive that was not unpacked and contained the remaining 10 files of interest, in chronological order of delivery are as follows:
- Delivery 1 – docs.rar: Created on 25 December 2017 (22:28:49 IST), a RAR archive which contained “Letter.pdf” and was deleted after unpacking was complete.
- Delivery 2 – Letter.pdf: Created on 25 December 2017 (22:29:50 IST), a minute after Delivery 1, and is the file contained within it. Arsenal’s summary of the document is as follows:
Alleged letter from “Ki” to “A” on October 17, 2017. Includes congratulations on Maoist party’s 13th anniversary and directs “A” to have a “picnic” regarding the work of Anti-Fascist Front. This document is in Hindi. (sic)
- Delivery 3 – Final_Dispatch.rar: Created on 27 December 2017 (21:23:45 IST), a RAR archive which contained “Final_Dispatch.pgp” and was deleted after unpacking was complete.
- Delivery 4 – Final_Dispatch.pgp: Created on 27 December 2017 (21:30:55 IST), seven minutes after Delivery 3, and is the PGP-encrypted file contained within it.
- Delivery 5 – mohila meeting jan.rar: Created on 11 January 2018 (11:39:40 IST), a RAR archive which contained “mohila meeting jan.pdf” and was deleted after unpacking was complete.
- Delivery 6 – mohila meeting jan.pdf: Created on 11 January 2018 (11:42:02 IST), less than three minutes after Delivery 5, and is the file contained within it. Arsenal’s summary of the document is as follows:
Alleged “mohila” (women in Hindi/Bengali) meeting minutes from January 2, 2018. Contains a list of Maoist party members, names of some Jawaharlal Nehru University ex-student leaders, and names of organizations like “JAC”, “JAGLAG”, “IAPL”, “CPDR”, and “DSU”. Mentions “Intensify tactical training for women PLGA members including booby traps/directional mines” and contains suggestions from “SG” regarding various matters. This document is in English. (sic)
- Delivery 7 – Accounts2k17.rar: Created on 1 February 2018 (22:47:19 IST), a RAR archive delivered alongside “Accounts2k17.txt” and then deleted.
- Delivery 8 – Accounts2k17.txt: Created on 1 February 2018 (22:48:48 IST), a minute and a half after Delivery 7, and is the file contained within it. Arsenal’s summary of the document is as follows:
Alleged details of funds transferred amongst Maoist party members. Contains details of transfers involving “Milind”, “Surendra”, “Shoma”, “Sudhir”, “Anand”, “Rona”, “Arun”, “VV”, and others. This text file is in English. (sic)
- Delivery 9 – IMPCorres.rar: Created on 11 February 2018 (15:41:17 IST), RAR archive containing “for your drafts.txt”, “Letter_to_GN_30July.pdf”, “ltr_CC_2_P.pdf”, “Received Naveen.doc”, “special.doc”, “JP resolution.doc”, “Letter to G.doc”, “Loans to be cleared and future programmes.xls”, “Note.doc”, and “Report on Gautam Navlakha.doc” (their contents are detailed below). This archive was never unpacked[12], and hence not deleted.
- Delivery 10 – NXPICS.rar: Created on 24 February 2018 (02:13:23 IST), a RAR archive renamed to DKComrades.rar, never unpacked, which appears to contain photographs of Maoist party PLGA guerrillas.
- Delivery 11 – ltr_from_Prakash.rar: Created on 2 March 2018 (01:31:00 IST), a RAR archive containing “Ltr_from_Prakash.pdf”, never unpacked, and summarised by Arsenal as follows:
[Ltr_from_Prakash.pdf] is an alleged letter from “Prakash” to “Rona”. Gives approval of a program on “Naveen Babu” at JNU. Refers to “Surendra”, “Sudha”, “Gadchiroli”, “Mahesh Raut”, and “Sudhir”. Mentions that the Bhima Koregaon movement is getting weaker and discusses party initiatives to strengthen it in BJP-ruled states, in order to hit the BJP in 2019 elections. Also mentions using PGP to exchange messages and destroying the letter immediately so that the enemy does not get ahold of it. This document is in Hindi. (sic)
Looking at the file names above together illustrates ModifiedElephant’s methodology of delivery. The 10 files further contained within the .rar archive created in Delivery 9 (below termed unretrieved files 1-10) in no particular order (as they were transferred collectively in the archive and have no date of creation due to never being unpacked on the system), as summarised by Arsenal, are as follows:
- Unretrieved File 1 – for your drafts.txt:
A text file that mentions “For your drafts use only” along with an email account username and password. This text file is in English. (sic)
- Unretrieved File 2 – Letter_to_GN_30July.pdf:
Alleged letter from “Sudarshan” on July 30, 2017 to “Gautam Ji”. Mentions state repression and says “The CC is well aware of the ground realities and difficulties faced by our comrades and party activists from CLC, PUDR, CDRO and other civil rights organizations while they are on FF missions in Bastar.” Also mentions contacting Comrade Surendra and defeating “fascist forces both politically and otherwise”. This document is in English. (sic)
- Unretrieved File 3 – ltr_CC_2_P.pdf:
Alleged letter from “dada” (brother in Hindi/Bengali) to “Prashant” on February 10, 2017 on Maoist party Central Committee letter head. Mentions state repression and problems in communicating. Requests that legal work be sped up for particular jailed activists. Shares concerns about “Sai” and the present situation of “CRPP” in Delhi. Also requests that “SG” call on the “safe number” on particular days and times before the “final hearing”. This document is in English. (sic)
- Unretrieved File 4 – Received Naveen.doc:
Alleged letter from “Anand” on May 7, 2015 as a reply to a letter from “Naveen”. Mentions problems coordinating with “legal mass” organizations in urban areas and updates on various military matters. Concludes with “Please destroy immediately after reading”. This document is in English. (sic)
- Unretrieved File 5 – special.doc:
Alleged letter from “Mahesh” to “Comrade General Secretary” of the Maoist party. The letter writer complains about his expulsion from the party while jailed, and mentions that while he broke under torture, he “guarded the major secrets”. This document is in English. (sic)
- Unretrieved File 6 – JP resolution.doc:
Document containing possibly obfuscated text as well as four sets of contact information. (sic)
- Unretrieved File 7 – Letter to G.doc:
Alleged letter to “Comrade” that mentions coordination of international Maoist movements. Contains details about meetings held in 2010 (Greece), 2011 (Germany) and 2012 (Greece). Includes suggestions provided at the last meeting. This document is in English. (sic)
- Unretrieved File 8 – Loans to be cleared and future programmes.xls:
Spreadsheet that lists “Programmes” (“All India Cordination against Military Deployment”, “Maoism Seminar”, etc.) and expenses, as well as loans which need to be paid back urgently. This spreadsheet is in English. (sic)
- Unretrieved File 9 – Note.doc:
Document which contains what appears to be a preliminary secret encoding of cities, date/times, individuals names (including “VV” and “Anand Teltumbde”), organization names, and passwords. This document is in English. (sic)
- Unretrieved File 10 – Report on Gautam Navlakha.doc:
Document which contains “A report on Gautam Navlakha (GN)”. This document includes a history of various interactions with “GN”. Mentions “VV” multiple times – for example: “He again walked out after his attempts to convince VV and others failed.” This document is in English. (sic)
The report also explained the process of the attacks, using the delivery of one ‘additional file of interest’ “mohila meeting jan.pdf” as an example of how the RAT would launch itself automatically on start up, as explained in Caravan Report II, and allow the attacker to directly control the command line. The command history also contains a tell-tale syntax error, which the report highlights as “consistent with an attacker making a mistake and then correcting that mistake.”
5. Arsenal Consulting Report III – Surendra Gadling: Common Attacker, Common Techniques
21 June 2021: Arsenal was retained by Surendra Gadling’s defence team after he was provided access to a copy of his hard drive, which formed the basis of Arsenal’s forensic examination alongside his Yahoo email. The executive summary of the report is as follows:
Arsenal’s analysis in this case has revealed that Surendra Gadling’s computer was compromised for just over 20 months by the same attacker[13] identified in Reports I and II. The attacker responsible for compromising Mr. Gadling’s computer had extensive resources (including time) and it is obvious that their primary goals were surveillance and incriminating document delivery. Arsenal has effectively caught the attacker red-handed, based on remnants of their activity left behind in file system transactions, application execution data, and otherwise. It is important to note that Arsenal has also recovered communications with the attacker’s command and control server from Mr. Gadling’s computer. Arsenal has connected the same attacker to a significant malware infrastructure which was deployed over the course of approximately four years[14] to not only attack and compromise Mr. Gadling’s computer for 20 months, but to attack his co-defendants in the Bhima Koregaon case and defendants in other high-profile Indian cases as well. It should be noted that this is one of the most serious cases involving evidence tampering that Arsenal has ever encountered, based on various metrics which include the vast timespan between the delivery of the first and last incriminating documents on multiple defendants computers.
Surendra Gadling’s computer was compromised on 29th February 2016 after receiving a series of emails containing NetWire (the same RAT that was used to infect Rona Wilson’s system) and remained compromised till a complete Windows reinstallation on 2nd November 2017 effectively knocked the attacker off the system. The reinstallation took place 5 months before police seizure on 17th April 2018, the same day co-accused Rona Wilson’s devices were seized. The chain of events leading up to 2nd November 2017 as recovered by Arsenal is as follows:
- 12 February 2016: Gadling receives two emails containing NetWire in different packages, one from Harshal Lingayat at 9:13PM and the next from Prashant Rahi at 11:54PM. It is pointed out that by this time, the malware infrastructure has spread significantly in the network of targeted activists, leading to the compromise of their emails.
- 18 February 2016: Gadling receives another email containing the RAT, this time from the compromised email of Arun Ferreira, another co-accused.
- 29 February 2016: All three emails from the above three senders contained identical installation scripts for NetWire, one of which was run on the 29th and executed a series of commands leading to the opening of a decoy document and NetWire being launched and made persistent parallelly. The IP address of the C2 server that the malware connected to upon launching has been associated with two of the attacker’s hostnames crucial to the case, and listed in Report I.
- 29 February 2016 to 3 December 2016: As with Rona Wilson’s computer, Surendra Gadling’s computer was infected with multiple NetWires, with at least 6 having been customised by 3 December 2016, and four more possibly existing on the disk that could not be confirmed. These samples connected to the same C2 server as mentioned in (3) above with identical configuration as in the case of Rona Wilson.
- 5 March 2016 to 22 October 2017: As with Rona Wilson, NetWire logs recovered by Arsenal revealed severe monitoring and surveillance of Gadling’s digital activity, including browsing websites, submitting passwords, composing emails, and editing documents. In this case as well the attacker made use of various additional tools to synchronise Gadling’s disk and attached drives (at least 15 of them, containing over 30,000 files) to their C2 server.
- 4 December 2016 to 22 October 2017: A hidden folder “Material” (similar to “Rbackup” on Rona Wilson’s computer) was created through NetWire on the 4 December 2016. It is into this folder that the 14 files relevant to the case against Surendra Gadling are delivered via NetWire and by no other means over the course of the next 10 months. The method of delivery followed the modus operandi established during the investigation of Rona Wilson’s devices: .rar archives are delivered, a more recent version of WinRAR is temporarily deployed to unpack them, and the archives and executables are deleted. As in the case of Wilson, this version of WinRAR used is different from the one present on Gadling’s system, which has a history of legitimate use, and was deployed specifically for these tasks by the attacker. Again, analysis of Object Identifiers revealed that none of these 14 files was ever interacted with in any legitimate way or that the folder they were contained in was ever opened. Following are the 14 files in chronological order of delivery.
- File 1 – Please read.txt: Created on 4 January 2017 (10:49:16.216 IST) via NetWire attack. Summarised by Arsenal as follows:
Alleged letter from “Prakash” to “com. Surendra.” Mentions sending important material including guidelines and decisions accepted in the last “ERB” meeting. Also mentions consolidating all bolshevik forces and organizing something on 6th April to remember the heroic and bold actions of the PLGA against the reactionary forces. This document is in English. (sic)
-
- File 2 – Dear Surendra.docx: Created on 20 January 2017 (12:32:57.555 IST) via NetWire attack. Summarised by Arsenal as follows:
Alleged letter to “Surendra.” Mentions not being able to meet as planned, legal defense work, and concern about “Com. Murgan.” Praises “Arun” and “Vernon” for their efforts to organize students. Mentions “Mahesh” and “Nandu” “have reached to us safely” and that some “PR’s” (professional revolutionaries) from “TISS” are also expected. Asks for an update about an upcoming IAPL conference and concludes by saying “… I will be reachable through com. Manoj.” This document is in English. (sic)
-
- File 3 – Prakash_MZ.pdf: Created on 20 February 2017 (22:52:30.336 IST) via NetWire attack. Summarised by Arsenal as follows:
Alleged letter from “Surendra” to “Com. Prakash.” Mentions that “Varavara Rao” has sent funds that Gadling is waiting for, and without that funding the fact finding team will not able to do their work. Discusses an “operation” involving comrades from the jungle and the supply of money and materials for guerilla war. Also mentions “Saibaba’s” release as a priority. This document is in Hindi. (sic)
-
- File 4 – Letter_MSZC.pdf: Created on 20 February 2017 (22:52:30.518 IST) via NetWire attack mere milliseconds after File 3. Summarised by Arsenal as follows:
Alleged letter from “Milind.” Mentions that under the guidance of “Com. Varavara Rao” and “Com. Surendra Gadling”, the attacks made in Gadchiroli and Chhattisgarh were successful and recognized all over India. Describes funds being sent by “Com. Varavara Rao” to “Com. Surendra” to make available to the letter recipient. Also mentions that “Com. Varavara Rao” and “Com. Surendra” will give guidance to the letter recipient at an upcoming meeting in Nagpur. This document is in Hindi. (sic)
-
- File 5 – Ltr_CC_2_P.pdf: Created on 08 March 2017 (21:33:10.636 IST) via NetWire attack. Summarised by Arsenal as follows:
Alleged letter from “dada” (brother in Hindi/Bengali) to “Prashant” on February 10, 2017 on Maoist party Central Committee letter head. Mentions state repression and problems in communicating. Requests that legal work be sped up for particular jailed activists. Shares concerns about “Sai” and the present situation of “CRPP” in Delhi. Also requests that “SG” call on the “safe number” on particular days and times before the “final hearing”. This document is in English. (sic)
-
- File 6 – Ltr_2_SG.pdf: Created on 14 March 2017 (22:13:05.421 IST) via NetWire attack. Summarised by Arsenal as follows:
Alleged letter from “Com. Varavara” to “Com. Surendra.” Mentions that his assurance to the organization has failed regarding Saibaba’s case, causing immense loss to the organization including fissures in urban cadre forces. Also mentions that the organization is angry with Surendra about a lack of funding. Directs Surendra to compensate the organization immediately, and to contact Chhattisgarh comrades to work towards breaking the confidence of the enemy. This document is in Hindi.
-
- File 7 – Reply_2_VV.pdf: Created on 21 March 2017 (12:40:16.062 IST) via NetWire attack. Summarised by Arsenal as follows:
Alleged letter from “Surendra” to “Com. Varavara Rao.” Mentions that he tried his best to keep his assurances regarding “Saibaba’s” case but judiciary sided with the enemy. Also mentions being in touch with senior CC comrades about an operation planned by “Varavara Rao.” Discusses a successful operation in Gadchirolli and lists places where deployment of enemy forces is lower and suitable for ambush. This document is in Hindi. (sic)
-
- File 8 – MoM-Final.pdf: Created on 16 April 2017 (23:29:53.150 IST) via NetWire attack. Summarised by Arsenal as follows:
Alleged letter from “Sudha” to “Prakash.” Includes minutes of an IAPL meeting held in Nagpur. Minutes mention offering urban cadres “packages” so that they don’t stay afraid after Saibaba’s arrest and “Com. Surendra” and “Stan Swamy” not being able to provide money. This document is in English.
-
- File 9 – Ltr_2704.pdf: Created on 05 May 2017 (14:45:52.540 IST) via NetWire attack. Summarised by Arsenal as follows:
Alleged letter from Comrade Surendra to Comrade Prakash outlining Surendra’s meeting on April 22, 2017 with a respected comrade from Chhatisgarh in Delhi, and handing over funds transferred via hawala for Bastar and Maharashtra “operations.” This document is in Hindi.
-
- File 10 – Dear Sudarshan da.pdf: Created on 15 May 2017 (14:22:48.842 IST) via NetWire attack. Summarised by Arsenal as follows:
Alleged letter from “SG” to “Sudarshan da.” Mentions interaction with “kishan da” regarding enemy movements in Bastar and other areas of interest. Mentions that “Com. Ramchandra” has been tasked with identifying soft targets. Discusses upcoming IAPL all India congress and Ambedkar Periyar Study Circle, and people dealing with IAPL-related matters. This document is in English. (sic)
-
- File 11 – CC_letter-08Jun.pdf: Created on 10 July 2017 (13:38:17.708 IST) via NetWire attack. Summarised by Arsenal as follows:
Alleged letter from “comrade M.” to “comrade Surendra.” The first part of this letter refers to complaints from the Delhi Women cadre and the party leadership taking gender bias, patriarchy, and authoritarian tendencies within the “MO leadership” seriously. The second part of this letter refers to setting up a day-long program on the theme of the 50th anniversary of the Naxalbari movement. This document is in English.
-
- File 12 – Ltr_16July17.pdf: Created on 22 July 2017 (13:45:33.017 IST) via NetWire attack. Summarised by Arsenal as follows:
Alleged letter from “Prakash” to “Surendra.” Mentions visiting Chennai to join “Com. Arun.” and that the party is taking measures to get jailed comrade “Adv. Murugan” released. Asks “Surendra” to speak with Adv to find youths to motivate them to become “PR’s” and for timely updates on “Com. Saibaba’s” case. This document is in English.
-
- File 13 – Dear Sudarshan da..pdf: (Not to be confused with file 10.) Created on 08 September 2017 (12:34:55.434 IST) via NetWire attack. Summarised by Arsenal as follows:
Alleged letter from “SG” to “Sudarshan da.” Mentions incorporating “R.Bhalla” into the “EC” in the upcoming IAPL meet and providing legal relief to imprisoned “Adv. Murugan.” Urges the collection of funds for IAPL work. This document is in English.
-
- File 14 – Ltr_2_SG-250917.pdf: Created on 30 September 2017 (22:43:53.771 IST) via NetWire attack. Summarised by Arsenal as follows:
Alleged letter from “Com. Prakash” to “comrade Surendra.” Mentions overwhelming enemy forces around “MH/CHH border.” Asks whether Surendra has received two pgp files containing action plan made with observations from senior leaders including “com. G.” Discusses strengthening student protests through “DUSU”, “JNUSU”, “APSC”, “AISF”, and “NSUI.” Concludes by mentioning getting assistance from Congress leaders, providing a phone number for “our friend”, and asking to be informed about “Sai” and “other senior comrades.” This document is in English.
- 22 July 2017: The attacker simultaneously accesses Rona Wilson’s and Surendra Gadling’s systems, both of which have been compromised by them at this point, and delivers one identical file “CC –Financial Policy.docx” to both of them, first to Wilson’s computer, then to Gadling’s, after which it is deleted from Wilson’s computer.
6. Arsenal Consulting Report IV – Rona Wilson: Pegasus and the Government’s Involvement
18 August 2021: In its fourth report relating to the instant case, and third based on the hard disk of Rona Wilson, the agency looked specifically for indicators of the infamous NSO Group spyware ‘Pegasus’ following Amnesty International and Citizen Lab’s report revealing those among the ‘BK16’ to be among those in a leaked list of targets. The methodology used in the report followed that of Amnesty International. The report confirmed the presence of Pegasus Indicators (reflecting attacks) on Wilson’s drive as well as a successful infection of his phone since at least 5 July 2017. Unlike Reports I and II, this one speaks about having examined only the hard disk and not the Cruzer blade. The executive summary of the report is as follows:
Arsenal found Pegasus Indicators on the Windows volume of Mr. Wilson’s computer in two iTunes backups from an iPhone 6s, serial C7JQL293GRY9 (hereafter, “Mr. Wilson’s iPhone 6s”). Timestamps associated with these indicators span from July 5, 2017 to April 10, 2018. According to the Amnesty International article “Forensic Methodology Report: How to catch NSO Group’s Pegasus”, the indicators found by Arsenal reflect not only Pegasus attacks, but successful Pegasus infection of Mr. Wilson’s iPhone 6s. It is important to note that during this entire timespan of Pegasus attacks and infection of Mr. Wilson’s iPhone 6s, the attacker identified in Arsenal Reports I, II, and III was using the NetWire RAT (Remote Access Trojan) on Mr. Wilson’s computer for purposes of both surveillance and incriminating document delivery. (sic)
7. Arsenal Consulting Report V – Stan Swamy: How Far Do the Roots Go Down?
11 December 2022: The latest and lengthiest of Arsenal’s reports was produced after Arsenal was retained by the defence team for the late Stan Swamy or Fr. Swamy), and was based on analysis of a copy of his hard drive, which was seized along with his computer by the Pune police dept. on 12 June 2019. The executive summary of the report is as follows:
Arsenal’s analysis in this case has revealed that Stanislaus Lourduswamy’s computer was compromised by the same attacker[15] identified in Reports I, II, and III over the course of three distinct campaigns, beginning on October 19, 2014 and ending upon the seizure of his computer by Pune police department on June 12, 2019. The attacker responsible for compromising Fr. Swamy’s computer had extensive resources (including time) and it is obvious that their primary goals were surveillance and incriminating document delivery. Arsenal has effectively caught the attacker red-handed (yet again), based on remnants of their activity left behind in file system transactions, application execution data, and otherwise. It is important to note that Arsenal has also recovered multiple types of communications with the attacker’s command and control server from Windows hibernation data on Fr. Swamy’s computer. Arsenal has connected the same attacker to a significant malware infrastructure’ which we now know was deployed over the course of over six years[16] to not only attack and compromise Fr. Swamy’s computer during the aforementioned timespan, but to attack his co-defendants in the Bhima Koregaon case and defendants in other high-profile Indian cases as well. It should be noted that this is one of the most serious cases involving evidence tampering that Arsenal has ever encountered, based on various metrics which include the vast timespan between the delivery of the first and last incriminating documents on multiple defendants computers. Arsenal’s findings in this report (and all of our others) can be replicated by competent digital forensics practitioners with access to the same electronic evidence. (sic)
Stan Swamy’s computer was first compromised on 19 October 2014, through a NetWire executable identical to those mailed to co-defendant Rona Wilson, on the 16th and 28th of November in the same year. Onwards, the system remained compromised for a period of 56 months until the seizure of his devices in 2019. In this period, Fr. Swamy was the victim of three separate NetWire campaigns, one of which was identical to those deployed against co-defendants Rona Wilson and Surendra Gadling. The chain of events, as reconstructed by Arsenal during this period, is as follows:
- 19 October 2014: Stan Swamy’s computer is compromised after an unwitting execution of a NetWire sample, embedded in a weaponised MS Word document, marking the beginning of the first campaign, called “itfuturisticspvt“. One sample launched and configured under this campaign was found by Arsenal. How the document was delivered to the system is not mentioned.
- 1 August 2016: The 2nd NetWire campaign, called “atlaswebportal” begins. This campaign was also used against co-defendants Rona Wilson and Surendra Gadling, and even had the same configuration (server, port and password). Four NetWire samples launched and configured under this campaign were found by Arsenal.
- 20 April 2019: The 3rd NetWire campaign, called “researchplanet” begins. Seven NetWire samples launched and configured under this campaign were found by Arsenal. This means that at least twelve RATs were deployed in Fr. Swamy’s system over the course of these three campaigns.
- 21 July 2015 to 11 June 2019: Fr. Swamy’s activity was heavily monitored through the Trojans, including browsing websites, submitting passwords, composing emails, and editing documents. The passwords stolen during this period also helped the attacker maintain persistence in Fr. Swamy’s emails, as well as in the cases of his co-defendants.
- 2 August 2016 to 9 June 2019: Following the modus operandi seen in the compromise of Rona Wilson and Surendra Gadling’s computers in reports I and III, Fr. Swamy’s disk and removable devices were synchronised with the attacker’s C2 servers using an open source file transfer client for Windows. At least 13 removable storage devices were synchronised in this manner, with over 24,000 files. Among the many scripts run by the attacker for this, each heavily obfuscated with “noise” which Arsenal stripped in their investigation, was one which contained the phrase “Now we can run XCOPY and fuck the machine!” The report highlights that this phrase had not been found on the other defendants’ devices. Another noteworthy observation was the customisation of the attacker’s infrastructure (such as their usernames, passwords, and folder names) to match the victim’s background, for e.g. “stan@socialstudies.zapto.org=41” specifically for Stan Swamy’s computer.
- 20 July 2017 to 5 June 2019: Following the modus operandi encountered in reports I, II and III, a hidden folder named ‘mydata’ (see ‘Material‘ on Surendra Gadling’s computer and ‘Rbackup‘ on Rona Wilson’s) was created through a NetWire attack on 20 July 2017. It is to this folder that ‘terrorism related documents’ were eventually delivered over the course of two subsequent NetWire campaigns, following the same methodology used in his two co-defendant’s cases: files were delivered first as .rar archives which were unpacked by a version of WinRAR temporarily deployed for this specific task, after which it was deleted along with the .rar archives. Again, the version of WinRAR present on the system with a history of legitimate use was different from the one used to unpack the planted files. A total of 57 such files were delivered to Fr. Swamy’s system in this manner, including deployed executables, folders, archives, .xlsx, .doc, .docx, and .pdf files. Several of these, the last four in particular, apart from the archives and WinRAR executables that the attacker normally deleted after use, were also delivered, deleted, redelivered, and thus modified by the attacker. Barring those, there were 44 documents (.xlsx, .doc, .docx, and .pdf) on Fr. Swamy’s system at time of seizure delivered to the hidden folder through NetWire, which were the ‘terrorism related documents‘ that he was accused of possessing. This is a significantly larger number than in the cases of his co-defendants and corresponds to the longer period of his system’s compromise and proportional severity of the attack against Fr. Swamy. As in the case of Rona Wilson, certain documents (listed below) were created using a version of MS Word not available on Fr. Swamy’s computer. Arsenal discovered NetWire “stacks” (memory-based remnants of the Trojan’s use) authoritatively demonstrating that the files were delivered using NetWire. Analysis of Object Identifiers showed that none of these files was ever interacted with in any legitimate way. A few notable documents are summarised below in chronological order of delivery:
- Notable Document 1 – Dear Vijayan dada.pdf: Created on 07/20/2017 (15:31:56.532 IST) via NetWire attack, using MS Word 2010. Purportedly authored by Fr. Swamy.
- Notable Document 2 – Dear Vijayan dada 05.10.17.pdf: Created on 10/12/2017 (14:44:22.498 IST) via NetWire attack, using MS Word 2010. Purportedly authored by Fr. Swamy. The document concluded with the phrase, “On the ground level there must be some action from your side to capture senior leaders of ruling BUP in the state and demand that the oppressive laws be done with.”
- Notable Document 3 – PLGA Status at Unity Congress.pdf: Created on 05/02/2019 10:49:04.165 IST) via NetWire attack. The document contains details about Peoples (sic) Liberation Guerrilla Army units, including numbers of personnel and types of available weapons in various Indian states.
- Notable Document 4 – Weeping Salandi – A PUCL Report on Communal Violence in Bhadrak, Odisha.pdf: Created on 05/05/2019 (14:37:13.674 IST) via NetWire attack. This file along with its contents was accessed through analysis of memory-based remnants of NetWire activity found in ‘buffers’. It is one of four files discovered this way.
- Notable Document 5 – PERSECUTED PRISONERS SOLIDARITY COMMITTEE.docx: Created on 05/05/2019 14:43:57.791 IST) via NetWire attack. This file was uploaded before “Inheritors of Naxalbari.docx” and after “Weeping Salandi – A PUCL Report on Communal Violence in Bhadrak, Odisha.pdf’, but none of its contents remained in the ‘buffer’ where it was accessed by Arsenal as its size was smaller than “Inheritors of Naxalbari.docx” and was thus completely overwritten. It is one of four files discovered through analysis of such ‘buffers’.
- Notable Document 6 – Inheritors of Naxalbari.docx: Created on 05/05/2019 (15:00:30.476 IST) via NetWire attack.
- Notable Document 7 – 15-5-17 Minutes.docx: Created on 05/05/2019 (16:27:37.649 IST) via NetWire attack.
The remaining 37 files were named: ‘2NS 0n Burning Forest_H.doc.pdf’, ‘2017-09-06_CC Stmnt Condemning Gauri Lankesh’s Assassination By BHF doc.pdf’, ‘2017-09-07_DKSZC Stmnt_Appeal 2 Sarv Adivasi and Bang Samaj_For Audio.doc.pdf’, ‘2017-9-26_CC stmt Eng on Rohingya.pdf’, ‘Eng_Ad_CC Message_13th Anniversary On Sept 21 2017.pdf’, ‘CMC letter on geedam.pdf’, ‘Concealment.pdf’, ‘Essential Underground Handbook (P M L Publishing).pdf’, ‘Secrets of RAW_v.k singh.pdf’, ‘YAESU VX-110 Operating manual.pdf’, ‘Dear Father Stan.docx’, ‘Gadchiroli Draft.docx’, subfolder ‘ILPS cananda’ (containing ‘canada.docx’, ‘18670937_$19227114867928_2573447111373526863_n.jpg’, ‘18671270_$19227054867934_3104159175336557907_n.jpg’, ‘18739731_51921167820280S_4997021182425215365_n.jpg’, ‘18767694_519227191534587_7182052400932737369_n.jpg’ and ‘18813678_519226461534660_949292694280721616_n.jpg’), ‘Documents accepted in the 2nd Conference of MLRO.pdf’, ‘The Strategy of the Indian Revolution MCC_Book pdf, WUCom Letter to ACs_2014.pdf’, ‘Mini manual of the urban guerilla2.pdf’, ‘Circular on Marriage, Family and Sex.doc’, ‘FinalPor-Eng.doc’, ‘Strategy and Tacties-E_May.doc’, ‘PB Tech CIR-H_10.Sep.pdf’, ‘Party Constiiion Hindi.pdf, Ltr2 Hyd 25Jan.pdf’, ‘For foreign delegates.pdf’, ‘Lr to com.P-Aug17.pdf’, ‘Plan for evaluation of LM-converted.pdf’, ‘Rome visit Ltr to CSAs TF-SJESS0-May’19.doc’, ‘Zonal, State and National Workshops(1).xlsx’, ‘MISEREOR (draft Proposal (1).docx’, ‘LM Report.doc’, ‘Rosemary Nag (1).pdf’, ‘Lr_toSCM-2105.pdf’
- 11 June 2019: The attacker began to perform an extensive clean-up of their malicious activities using NetWire, including crude anti-forensic activity, which was abruptly interrupted by a manual shutdown legitimately initiated by Fr. Swamy himself at 21:01:28 IST. Arsenal has highlighted the clean-up as “both unique and extremely suspicious given the computer’s imminent seizure” the following day on 12 June 2019. The clean-up included:
- Deletion of NetWire logs, scheduled attacks and malicious tasks, NetWire wrappers, scripts, surveillance resources such as a hidden staging area from which files from Fr. Swamy’s computer were synchronised with the attacker’s C2 server, and other tools including several NetWires.
- Creation of “noise”.
- Renaming of suspicious malicious folders to unsuspicious names such as “Desktop” and “OperaBak”.
The deletion of surveillance activity included one massive deletion of 14,313 files from the hidden staging area through a command “del /f /q /s” which has been highlighted by Arsenal for not only being a significant deletion but for being a “forceful, quiet and recursive” one. A similarly desperate command was used for the creation of “noise” in two folders where malicious activity had taken place, where files were copied using “copy /s /c /h /r /y“: recursively (/s), ignoring errors (/c), with hidden and system files (/h), with read-only files (/r), and suppressing any prompts regarding overwriting existing files (/y). Again, it should be noted that this activity was taking place the night immediately prior to the seizure of the device, and was abruptly interrupted by manual shutdown, before the attacker could send the NetWire “a1” control command for removing itself.
8. SentinelOne Report – A Decade of ModifiedElephant
9 February 2022: A report by another US based firm, AI-oriented security firm SentinelOne’s SentinelLabs, titled ‘ModifiedElephant APT and a Decade of Fabricating Evidence‘ and authored by Tom Hegel, that tied together all the attacks and operational history of the common attacker identified by Arsenal, was released. “Activists, human rights defenders, journalists, academics, and law professionals in India are those most highly targeted. Notable targets include individuals associated with the Bhima Koregaon case,” the report said.
This threat actor (APT stands for ‘Advanced Persistent Threat‘) was named “ModifiedElephant“, and following the indicators of their activity already identified by Arsenal, Sentinel was able to uncover an even longer history of activity—at least 10 years and counting at time of publication in 2022. As of February 2025, ModifiedElephant is still active. The executive summary of the report is as follows:
- Our research attributes a decade of activity to a threat actor we call ModifiedElephant.
- ModifiedElephant is responsible for targeted attacks on human rights activists, human rights defenders, academics, and lawyers across India with the objective of planting incriminating digital evidence.
- ModifiedElephant has been operating since at least 2012, and has repeatedly targeted specific individuals.
- ModifiedElephant operates through the use of commercially available remote access trojans (RATs) and has potential ties to the commercial surveillance industry.
- The threat actor uses spearphishing with malicious documents to deliver malware, such as NetWire, DarkComet, and simple keyloggers with infrastructure overlaps that allow us to connect long periods of previously unattributed malicious activity.
Sentinel worked towards and succeeded in expanding the modus operandi of ModifiedElephant, as had been clearly established in the first three Arsenal reports alongside other reportage:
- RAT Infection via Spearphishing: Use of commercial rats like NetWire/DarkComet, free email domains such as Gmail and Yahoo.
- Long term surveillance using open source tools: WinSCP for C2 synchronisation.
- Planting of fabricated incriminating evidence: .rar archives unpacked by temporarily deployed UnRAR into nested hidden folders.
- Clean-up/continued malicious activity leading up to the time of seizure of devices by state agencies: Crude/desperate anti-forensic activity, deletions, cancellations of scheduled tasks, or deliveries of important incriminating documents, before the seizure.
While the objective of ModifiedElephant’s attacks remained long term surveillance culminating in the planting of fabricated evidence leading up to and coordinated with the target’s arrest as analysed by previous investigators, Sentinel made significant expansions on their history of activity (traced back all the way to 2012), in their surveillance techniques and choice of malware. For instance, the report found that even before making their foray into commercially available RATs, ModifiedElephant made use of crude keylogging techniques to spy on targets, and that in addition to NetWire and DarkComet, also made use of the GM Bot and an unidentified Android Trojan delivered as APK (application) files described as an ‘ideal low-cost mobile surveillance toolkit.’
One of the most noteworthy conclusions of the report is the confirmation of a speculation that has remained consistent throughout the Arsenal reports: the surprisingly unsophisticated nature of ModifiedElephant’s attacks. The malware infrastructure used most often by the attacker was described as ‘unsophisticated and downright mundane.’ Their longer-lived techniques, such as the above-mentioned keylogging, have been described as extremely brittle to the point of being dysfunctional, technically unimpressive and likely to have been plagiarised. Following is an excerpt describing ModifiedElephant’s ‘Incubator keylogger’ (so named because of a term used in its code):
[The keyloggers], packed at delivery, are written in Visual Basic and are not the least bit technically impressive. Moreover, they’re built in such a brittle fashion that they no longer function. The overall structure of the keylogger is fairly similar to code openly shared on Italian hacking forums in 2012. In some ways, the Incubator keylogger is far more brittle than the code referenced above as it relies on specific web content to function.
The report also covered ModifiedElephant’s relations to other threat actors and malware infrastructures, including another Advanced Persistent Threat actor within India, called SideWinder, that operated alongside it with overlapping durations of activity as well as overlapping targets (both limited to phishing emails). Between February 2013 and January 2014, Rona Wilson was targeted by such emails by SideWinder. Pegasus, FinFisher, and Operation Hangover were also connected to the ModifiedElephant malware infrastructure.
9. The Wired – The Thrice Verified Link to Shivaji Pawar
6 June 2022: US based Tech magazine WIRED releases a report titled, “Police Linked to Hacking Campaign to Frame Indian Activists,” in reference to ModifiedElephant’s attacks against those arrested in the Bhima Koregaon/Elgar Parishad case. The report begins with an anonymous account by an employee of an unnamed email service provider, who confirmed that a recovery email and phone number were added to the accounts of Rona Wilson, Varavara Rao and Hany Babu at the time of compromise: a backway for the hacker to regain access to the systems and the mails. These recovery contacts belonged to an IPS officer who would later be named by SentinelOne’s Juan Andres Guerrero-Saade, along with Tom Hegel, at the upcoming Black Hat security conference—Shivaji Pawar!
These accounts, exclusively given to WIRED on the condition of anonymity, are then twice more confirmed by named sources: Scott Railton at the Citizen Lab (who previously collaborated with Amnesty International on their report on the hacking nexus targeting Bhima Koregaon defendants), and security researcher Zeshan Aziz.
10. KrebsonSecurity – The End of NetWire and a Lead to ModifiedElephant
9th March 2023: As per a report by the independent cybersecurity news & investigation website, KrebsonSecurity, the US FBI seized the domain ‘worldwiredlabs[.]com’ for the distribution of NetWire, after a Croatian national was arrested for allegedly administering it, & a computer server was seized in Switzerland for allegedly being in use for the same. None of the three authorities provided any information about the accused or the basis of his arrest, KrebsonSecurity’s investigation nevertheless covered the case in based on both information available in the public domain, interviews with the accused, as well detailed digital sleuthing.
References/Links
- https://caravanmagazine.in/law/did-pune-police-tamper-evidence-against-bhima-koregaon-accused
- https://caravanmagazine.in/politics/bhima-koregaon-case-rona-wilson-hard-disk-malware-remote-access
- https://www.newslaundry.com/2021/01/02/bhima-koregaon-case-three-years-of-legal-and-rights-violations
- https://krebsonsecurity.com/2023/03/whos-behind-the-netwire-remote-access-trojan/
- https://drive.google.com/drive/folders/1QoonWsBbpWiJFaIl2zgLN6l0rxezNHHa?ref=static.internetfreedom.in
- http://books.ms/main/B3FC3CA9814A81AE801C34AC123DAB88
- https://www.satp.org/south-asia-intelligence-review-Volume-17-No-10
- https://thewire.in/politics/modi-assassination-plot-letter-danger-democracy
- https://www.amnesty.org/en/latest/research/2020/06/india-human-rights-defenders-targeted-by-a-coordinated-spyware-operation/
- https://www.ripe.net/ripe/mail/archives/anti-abuse-wg/2016-July/003450.html
- https://www.amnesty.org/en/latest/research/2021/07/forensic-methodology-report-how-to-catch-nso-groups-pegasus/
- https://assets.sentinelone.com/sentinellabs-apt/modified-elephant-apt
- https://securityintelligence.com/gm-bot-alive-upgraded-now-android-m/
- https://www.virustotal.com/gui/file/4dbb14ff2836733b34594956c4234d2a54c04257710dd31a0884b1926d35d7bc
- https://www.theverge.com/2015/1/21/7861645/finfisher-spyware-let-bahrain-government-hack-political-activist
- https://web.archive.org/web/20210226131047/https://paper.seebug.org/papers/APT/APT_CyberCriminal_Campagin/2013/NS-Unveiling-an-Indian-Cyberattack-Infrastructure_FINAL_Web.pdf
[1] Only a small component of the gross procedural violations made during the entire investigative process, including but not limited to the illegal nature of the raids themselves, which were conducted against twice denied warrant applications. This and other violations had been compiled by Prateek Goyal in a report for Newslaundry in January 2021.
[2] In March 2023, a Croatian national was arrested for distributing the RAT, and its website was seized by the US FBI. Though charges have not been proved (or even framed) against the accused in the instant case so far, it is through this website that NetWire was sold for 11 years between its creation in 2012 and its seizure in 2023, and is likely where Rona Wilson, Surendra Gadling and Stan Swamy’s common attacker, the notorious ModifiedElephant, purchased it from as well. SentinelOne’s report on ModifiedElephant’s history of attacks suggested potential ties between the APT and the commercial surveillance industry.
[3] “The incriminating documents were delivered to a hidden folder on Mr. Wilson’s computer by NetWire and
not by other means.” (p. 7)
[4] “One method that can be used to assist in determining whether a particular document has ever been opened on a particular computer is to review the NTFS file system’s “object identifier” (a/k/a $OBJECT_ID) attributes for that document. Object identifiers are normally assigned to documents when they are either created or first opened. In this case, none of the top ten documents have object identifiers.” (p. 7)
[5] This is hard evidence of technical impossibility, and should be viewed in addition to the pre-existing arguments for the implausibility of Wilson or any of his co-accused having been either the authors or intended recipients of the letter based on its linguistic analysis: Alpa Shah in her book The Incarcerations (p. 286-288) analysed the language and structure of the letter and highlighted notable inconsistencies both within its internal language and in its use of real names of people and weapons, both gross violations of standard Maoist practice of using exclusively codenames for correspondence; Dr. Ajai Sahni in his report Urban Maoist Fakery for the South Asia Terrorism Portal said, the letters have all the hallmarks of mischievous fabrication… It is unlikely that these letters (yet to be placed before the courts, but widely circulated in the media) will stand up to judicial scrutiny either. Crucially, the language, content and character of this purported correspondence militates against everything that is known about the Maoists.’ The logico-linguistic analysis of the letters by various experts indicates fabrication, in addition to the NetWire implantation discovered in Arsenal’s investigation.
[6] Corrected to at least six years in the fifth Arsenal report, and since at least 2012 as per the SentinelOne ModifiedElephant investigation.
[7] Amnesty International Report.
[8] Access to Rao’s seized hard drive can clarify how his email was compromised.
[9] Also used in the case of the ‘top 10’ along with various other cyber tools.
[10]12 files including the .rar file that contained 10 more.
[11] The files were located in an AVCHDCoder folder, which should only contain data related to the use of the eponymous program, used for video file conversion. Arsenal highlighted this to be ‘suspicious’.
[12] It should be noted that none of the deliveries from this point onward were ever unpacked, until the tenth and final ‘top ten most incriminating document’, Ltr_2_Anand_E.pdf was created on 6th April 2018.
[13] Later termed ModifiedElephant in SentinelOne’s 2022 report.
[14] Corrected to at least six years in the fifth Arsenal report, and since at least 2012 as per the SentinelOne report.
[15] Earlier termed the ModifiedElephant in Sentinel’s report published February the same year.
[16] Since at least 2012 as per SentinelOne’s report.
SUPPORT US
We like bringing the stories that don’t get told to you. For that, we need your support. However small, we would appreciate it.





